Stop Identity Threats Before They Become Breaches
Actionable Identity Threat Intelligence to Prevent Breaches.
Identify, track, and remediate exposed credentials found on the DarkWeb
Darkwatch delivers continuous, real-time insight into emerging threats by scanning billions of records from breaches, stealer logs, and dark web sources. Equip your team with the tools to understand the risk, prioritize response, and stay ahead of attacks before they escalate.
Uncover the root cause and scope of the incident
CYBERSECURITY Solutions
We track exposed logins, passwords, tokens, and session data tied to your employees, customers, vendors, and domains — before attackers can use them.
Enterprise Protection
Track exposed logins, domains, and users. Get ahead of targeted attacks with actionable alerts.
Consumer risk protection
Bounce back from a cyberattack and restore day-to-day operations with minimal downtime.
data partnerships
Looking for MSP/MSSP Support?
Bounce back from a cyberattack and restore day-to-day

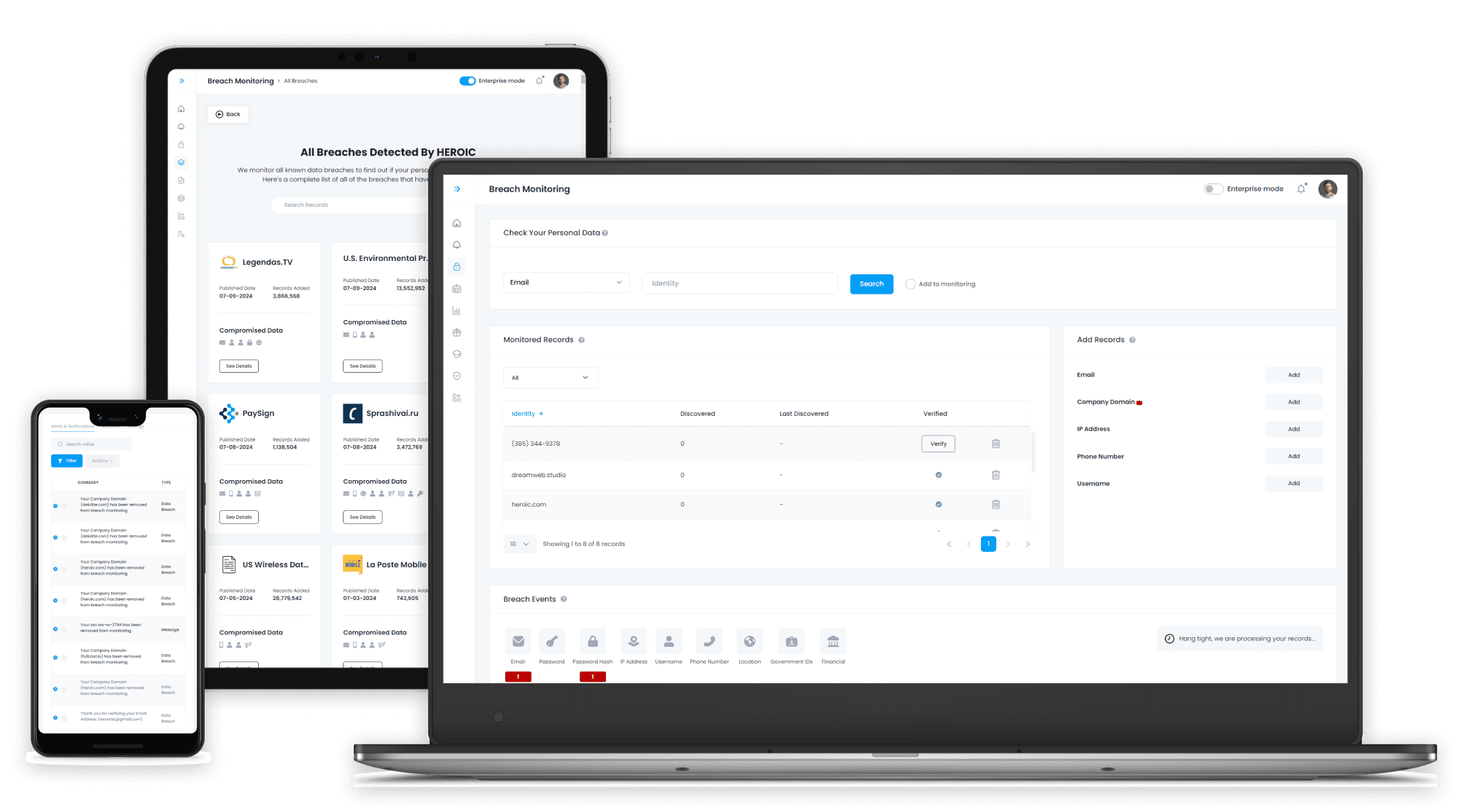
Protect Your Organization From the Risks You Can’t Afford to Miss
Today’s threats move fast but your defense has to move faster. HEROIC is built for scale, powered by AI, and designed for security teams who need clarity, speed, and control. Whether you’re protecting 50 users or 50,000, our platform adapts to your needs and evolves with every breach.
Smarter than alerts. Faster than threats.
The future of threat resolution starts here
Real-Time Intelligence and Early Intervention
Complete Visibility Into Identity Exposure
Access high-fidelity breach data across public, private, and covert sources to proactively uncover credential risks before they’re exploited.
Contain External Risk Across Your Ecosystem
Maintain Compliance and Audit Readiness
Continuously align with frameworks like NIST, HIPAA, and GDPR through traceable identity monitoring and policy enforcement.
Organization-Wide Identity Risk Coverage
Reduce Security Stack Complexity with a Unified Platform
Automate Threat Management and Resolution
Reduce Alert Fatigue with Automated Filtering and Resolution
Seamless Integration Into Your Current Security Ecosystem
Monitor Identity Risk Across All Vectors
Access the worlds largest database of breached credentials.
Get instant access to billions of exposed credentials collected from breaches, stealer logs, and underground sources. Continuously updated and deduplicated, this unmatched dataset helps you uncover compromised identities across your organization, reduce risk at scale, and stay ahead of threats long before they become incidents.
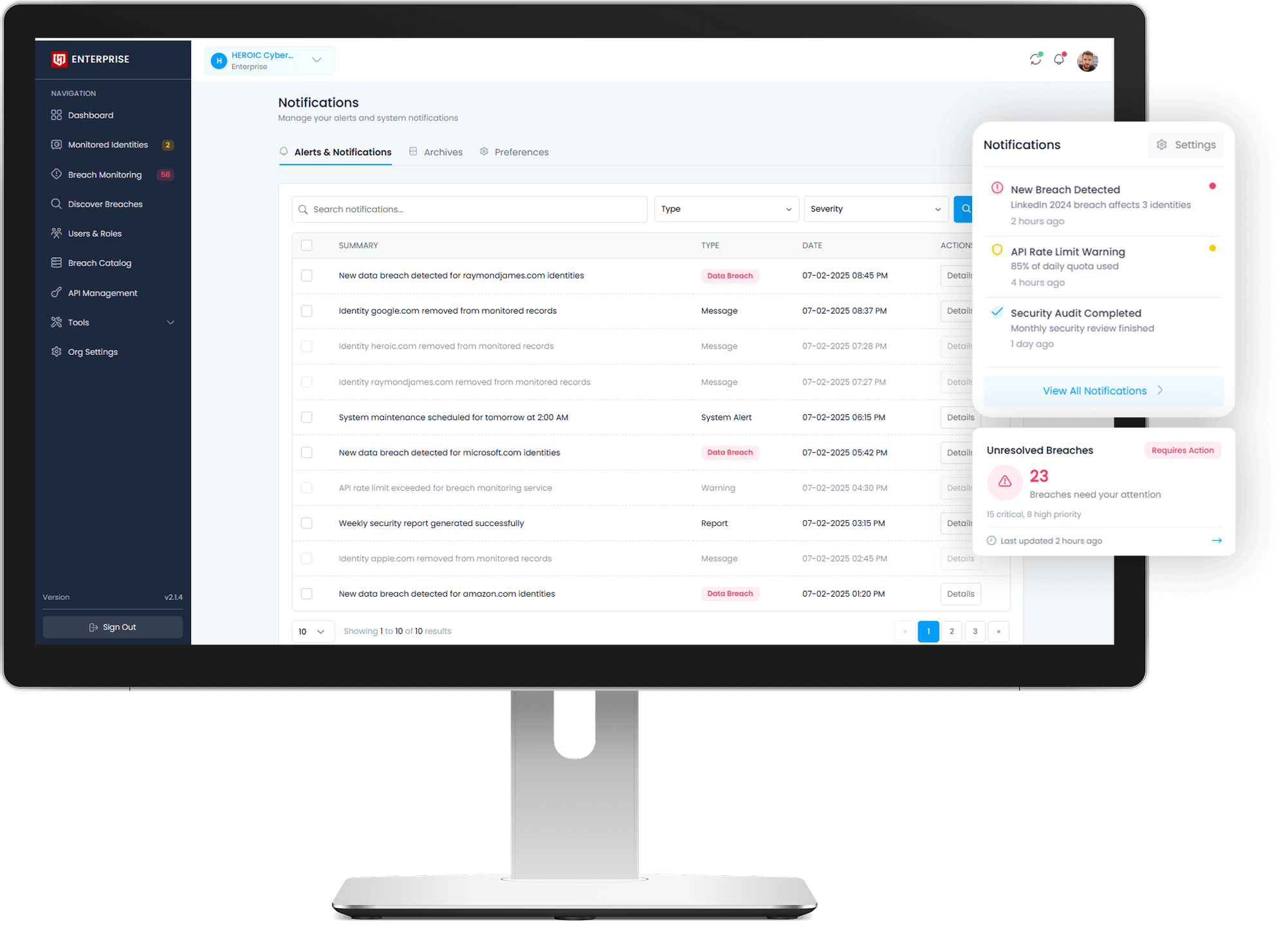
Explore All Breaches
Stop Guessing. Start Seeing.
Get verified breach intelligence before attackers do — and take action while others are still reacting.






















/includes/qr-code.png)