HEROIC EPIC™








Protect Your Organization from Credential Stuffing
Access to over 400 billion+ breached records
Intelligent, Real-Time Protection
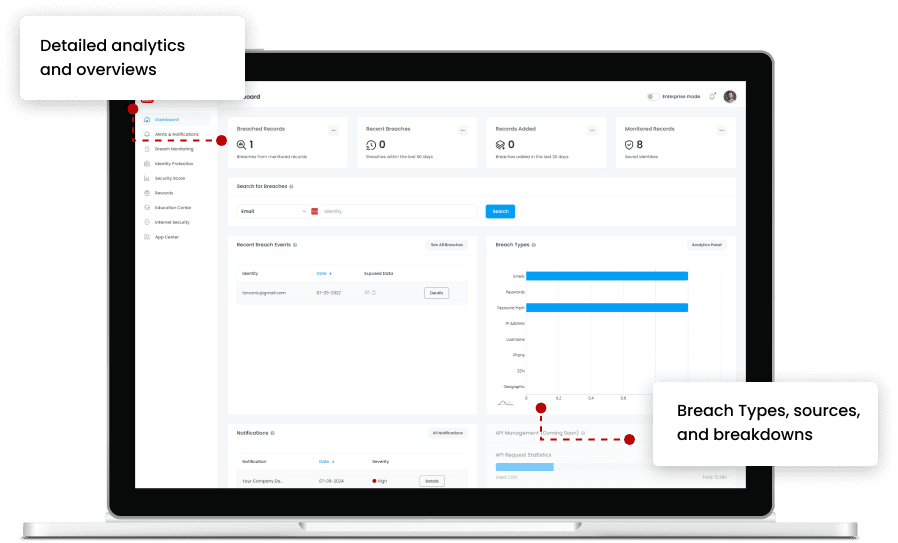
Advanced Results and Information
Uncover Vulnerabilities & Protect
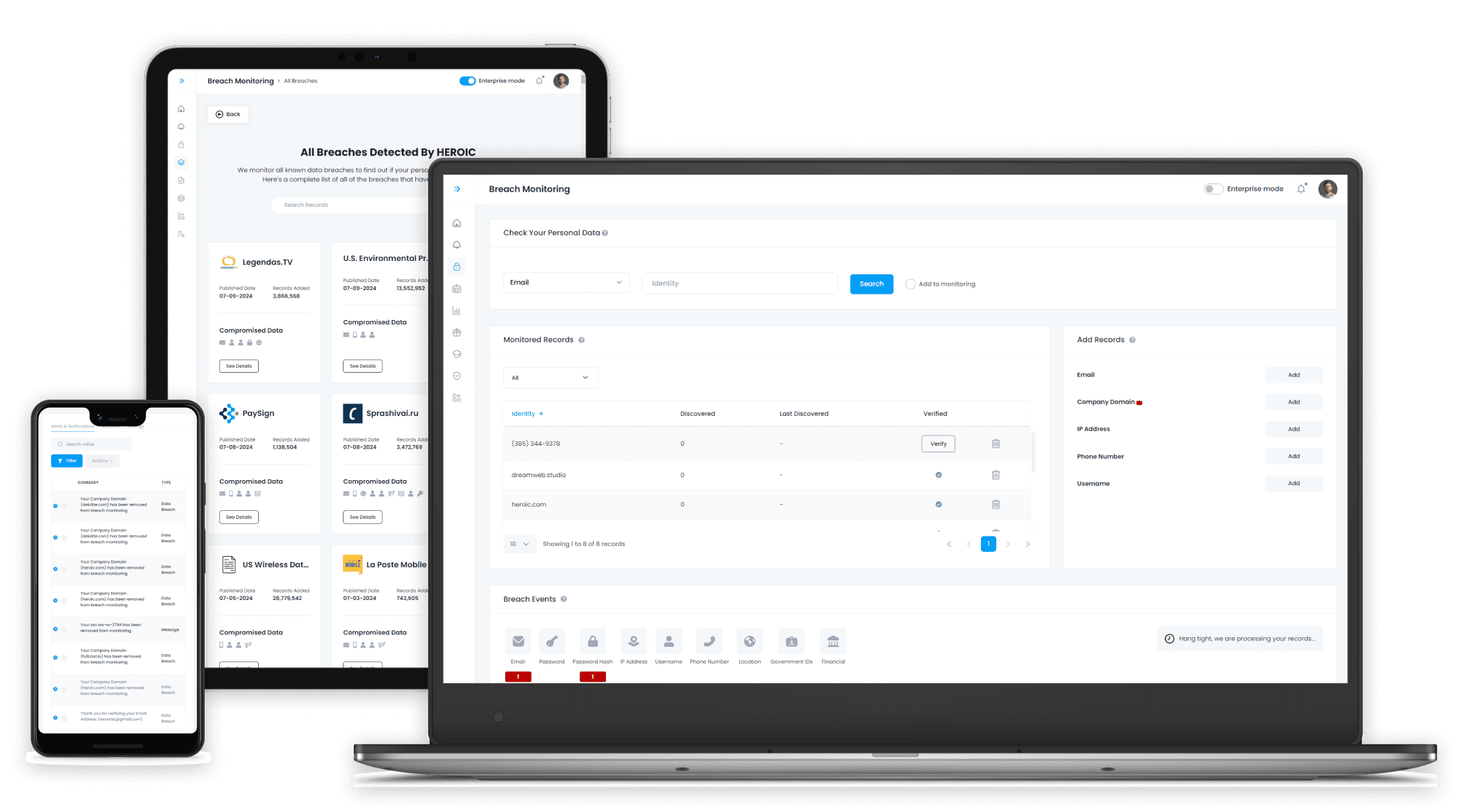
Advanced Breach Searching and insights
Data holds no value unless it’s actionable. Our database will show email addresses, passwords (including hashes), usernames, IP addresses and any other information that may have been exposed for your team to properly remediate.
Access to DarkHive™
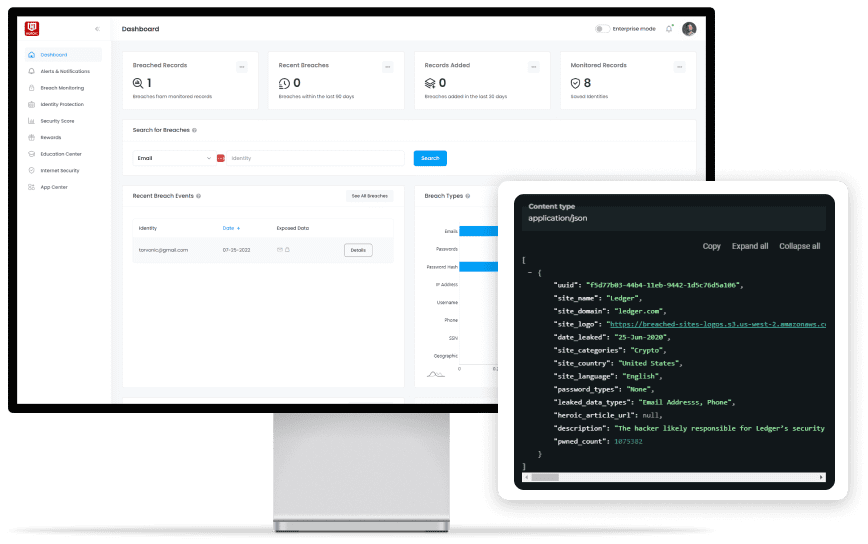
Database Leaks
Compromised databases with sensitive information like usernames, passwords, and personal data exposed due to breaches.
Stealerlogs
Logs generated by malware capturing stolen credentials, browser data, and personal information from infected devices.
Pastebins
Combolists
Real time Notifications and Alerts
Data holds no value unless it’s actionable. Our database will show email addresses, passwords (including hashes), usernames, IP addresses and any other information that may have been exposed for your team to properly remediate.
Customized Roles and Permissions
Strong cybersecurity teams rely on more than one person. EPIC offers users the ability to create numerous roles and permissions, allowing multiple departments to gain insight into the organization’s vulnerabilities and strengths.






/qr-code.png)