HEROIC GUARDIAN
Unified protection for home users and families









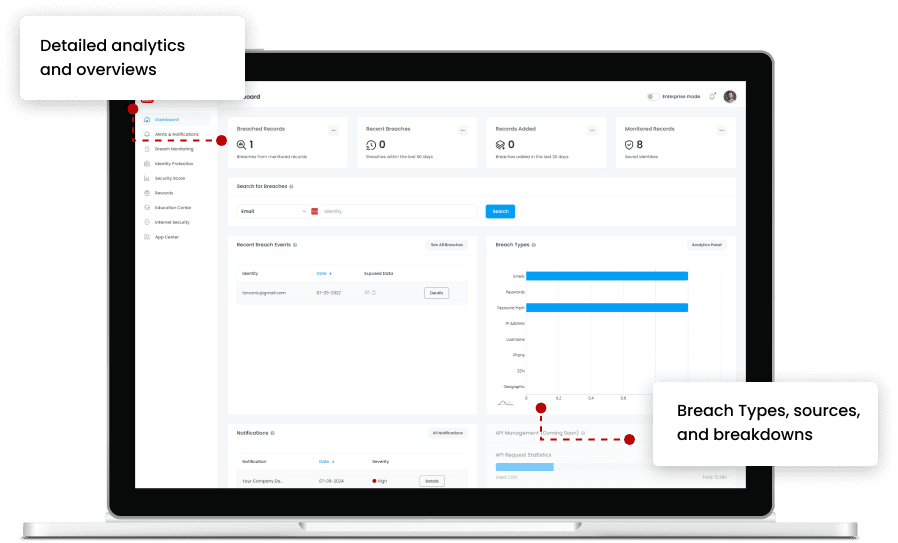
360 Protection For The Entire Family

Protect & Monitor Your Identity
See when your Emails, Passwords, Usernames, Phone Numbers, and IP Addresses have been compromised on the Dark Web.

Secure your Internet and Filter websites
Connect your router to HEROIC’s Internet Security to filter out domains, keep your network secure, and choose what you want people to see.

Protect Yourself against new Cyberthreats
Get Access to core features to protect you and your family from hackers and compromised credentials.
More than Antivirus
Breach Monitoring
Get Instant Details when Your data is Leaked on the Dark Web
Stay ahead of cyber threats with real-time breach monitoring. Guardian scans the dark web to identify when your data has been leaked, providing instant details about the exposure. From compromised passwords to sensitive information, our platform empowers you to act swiftly and mitigate risks before they escalate.
Identity protection
Get alerts when your Social Security has been Used
Protect your personal identity with powerful alerts for suspicious activity. Whether it’s your Social Security number being used without authorization or other critical identity breaches, Guardian notifies you immediately so you can take the steps necessary to safeguard your information and prevent fraud.
Identity protection
Secure your internet with Filters, Domain Blocking, and more.
Ensure a safer online experience with advanced security tools. Guardian offers customizable internet filters, domain blocking, and other features to protect your network from malicious sites and content. With Guardian, you can browse confidently, knowing your digital environment is secure.

Education Center
Stay up to date on new threats and how to stay safe
Stay informed and prepared with Guardian’s comprehensive education center. Learn about emerging cyber threats, security best practices, and tools to protect yourself online. By staying informed, you’ll have the knowledge needed to navigate the digital world securely and confidently.
Core Platform Features
Personalized AI
Largest Hack Database
Robust API Integration
Integrated Apps
Real-Time Alerts
Data Breach Search
Security Education
Internet Monitoring & Filters
Identity Theft Protection
Security Score
Antivirus
VPN

Kaidown
In March 2018, Kaidown, a now-defunct Thai general business website, suffered a data breach that affected 858,277 users. The compromised data included email addresses and plaintext passwords. Users are strongly advised to change their passwords and be wary of any services that fail to use password encryption.

AccGame
In August 2022, AccGame, a Vietnamese platform selling PUBG Mobile Game Accounts, suffered a data breach exposing approximately 31,000 records containing over 5500 unique email addresses, usernames, phone numbers, and MD5 hashed passwords. This incident highlights the importance of strong cybersecurity measures to protect sensitive customer data and prevent future breaches, as even hashed passwords can compromise security if compromised.

Aquile Nere
In November 2022, Aquile Nere, an Italian e-commerce platform specializing in military-style clothing, tactical gear, and outdoor equipment, experienced a data breach exposing approximately 3,600 records containing nearly 3,200 unique email addresses, full names, and genders. This incident underscores the importance of implementing robust cybersecurity measures to protect sensitive personal information from unauthorized access and potential breaches.

RUaH Music Magazine
In August 2018, RUaH Music Magazine, a now-defunct Polish gallery for music and artists, suffered a data breach that affected 155,192 users. The compromised data included email addresses and MD5 password hashes. Given the outdated nature of MD5, users should update their passwords and avoid reusing them across services.

ProWrestlingFans
In March 2018, ProWrestlingFans, a now-defunct U.S.-based pro wrestling news and fan community site covering WWE, TNA/Impact, ECW, and more, suffered a data breach that affected 254,430 users. The compromised data included email addresses and MD5 password hashes. Users should update any shared passwords, as MD5 hashes are vulnerable to cracking.

QArchive
In August 2018, QArchive, a now-defunct U.S.-based website showcasing archived software downloads, suffered a data breach that affected 118,312 users. The compromised data included email addresses and MD5 password hashes. Affected users should rotate their passwords and avoid reusing them on other services.

Red Colony
In August 2018, Red Colony, a U.S.-based international symposium site bringing together students and professionals interested in colonizing and terraforming Mars, suffered a data breach that affected 154,995 users. The compromised data included email addresses and MD5 password hashes. Due to the insecure nature of MD5, affected users should update their passwords immediately.

Archslate
In June 2022, Archslate suffered a data breach exposing approximately 100,000 records containing over 1600 unique email addresses, user names, phone numbers, and bcrypt hashed passwords. This underscores the critical need for robust cybersecurity measures to protect sensitive personal information from unauthorized access and potential breaches.

Gametag
In July 2018, Gametag, a now-defunct U.S.-based marketplace for buying and selling video game accounts—primarily Xbox and MMO credentials—suffered a data breach that affected 158,375 users. The compromised data included email addresses and plaintext passwords. Affected users should change passwords and be vigilant against account theft or misuse.

Rabota.bg
In July 2020, Rabota.bg, the top job board in Bulgaria offering employment listings and career services nationwide, suffered a data breach that affected 361,127 users. The compromised data included email addresses and MD5 password hashes. Users should change passwords and remain alert to potential phishing or account compromise.

Waffle Factory
In February 2025, Waffle Factory—a popular fast-casual waffle restaurant franchise originating from Belgium—suffered a data breach that affected 251,808 users. The compromised data included phone numbers, email addresses, full names, birthdates, and dates. This incident highlights the critical importance of robust cybersecurity measures to protect customers' personal information and maintain their trust in consumer-facing brands.

Kütle nedir
In August 2018, Kütle nedir, a now-defunct Turkish educational website focused on physics, suffered a data breach that affected 52,941 users. The compromised data included email addresses and MD5 password hashes. Users should change any reused passwords, as MD5 is an outdated and insecure hashing algorithm that can be easily cracked.

Christmas Time UK
In November 2017, Christmas Time UK, an ecommerce platform specializing in Christmas decorations, suffered a data breach affecting around 101 thousand unique records. The exposed data includes email addresses and passwords stored as plain text. Strong cybersecurity practices, including secure password storage, are essential to protect customer information.

QuinceanerasMagazine
In August 2018, QuinceanerasMagazine, the official site of Quinceañera Magazine—a U.S.-based bilingual publication helping families plan quinceañeras and other milestone events—suffered a data breach that affected 43,254 users. The compromised data included email addresses and password hashes stored in an unknown format. Users should reset passwords and be cautious about using platforms with unclear security standards.

Telegram InfernoLogsCloud #176 by .boxed.pw
On June 19, 2025, a stealer log titled @InfernoLogsCloud LOGS FREE#176 was shared on a Telegram channel. The log exposed around 13,165 email addresses, as well as plaintext passwords, homepage URLs, and system information on affected devices. This type of breach, stemming from infostealer malware, underscores the urgent need for proactive cybersecurity measures—including the use of password managers, antivirus protection, and routine system monitoring—to mitigate the risk of identity theft and further exploitation.

GasPriceWatch
In August 2018, GasPriceWatch, a now-defunct U.S.-based website for tracking gas prices and fluctuation levels, suffered a data breach that affected 315,436 users. The compromised data included email addresses and MD5 password hashes. Users should update passwords and move away from platforms using obsolete security methods.

Bloemendelivery
In June 2025, Bloemendelivery, a Netherlands-based e-commerce platform specializing in same-day flower delivery, suffered a data breach that impacted 24,256 users. The compromised data included email addresses and pHpass password hashes, potentially exposing users to account takeover risks if reused credentials were involved.

Telegram RusCloud 6-17-25 .boxed.pw
On June 19, 2025, a stealer log titled Logs_17 June was shared on a Telegram channel. The log exposed around 728 email addresses, as well as plaintext passwords, homepage URLs, and system information on affected devices. This type of breach, stemming from infostealer malware, underscores the urgent need for proactive cybersecurity measures—including the use of password managers, antivirus protection, and routine system monitoring—to mitigate the risk of identity theft and further exploitation.

Telegram BabaCloudLogs 6-19-25 .boxed.pw
On June 19, 2025, a stealer log titled @BabaCloudLogs { 479 } Cloud Logs 19.06.2025 was shared on a Telegram channel. The log exposed around 16,899 email addresses, as well as plaintext passwords, homepage URLs, and system information on affected devices. This type of breach, stemming from infostealer malware, underscores the urgent need for proactive cybersecurity measures—including the use of password managers, antivirus protection, and routine system monitoring—to mitigate the risk of identity theft and further exploitation.

Prima-Finden
In August 2018, Prima-Finden, a German online classified ads platform for free listings in categories like tickets, vehicles, electronics, children’s items, and services, suffered a data breach that affected 141,298 users. The compromised data included email addresses and password hashes stored in an unknown format. Due to the uncertainty around encryption strength, users should change their passwords as a precaution.




/qr-code.png)