HEROIC DARKWATCH™
Know exactly when your data appears on the dark web before attackers act.
Darkwatch delivers continuous, real-time insight into emerging threats by scanning billions of records from breaches, stealer logs, and dark web sources. Equip your team with the tools to understand the risk, prioritize response, and stay ahead of attacks before they escalate.
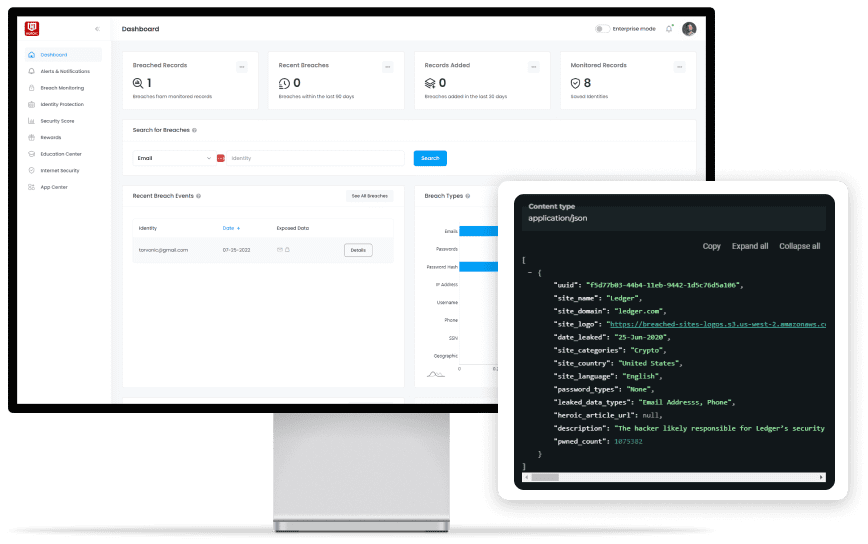
Stop guessing where you’re exposed
Search. Discover. REsolve.
With over 400 billion records and growing, Darkhive delivers the most comprehensive and actionable breach data available, all under one roof.

Detect Identity Threats Instantly
Continuously monitor the open, deep, and dark web for compromised credentials, stealer logs, and exposed identity data the moment it surfaces.

Filter Noise with Precision
Cut through the flood of breach data using advanced deduplication, intelligent correlation, and automated filtering that highlights only verified, high-impact threats.

Integrate Seamlessly Into Your Stack
Connect breach intelligence into your SIEM, SOAR, IAM, and other tools via robust APIs — accelerating deployment without disrupting your existing workflows.

Access Full PII for Actionable Response
Get the complete set of exposed information in every verified record including names, addresses, phone numbers, passwords, and other identifiers

Protect Across Your Ecosystem
Extend identity threat protection to internal users, remote employees, vendors, and third parties, securing your full attack surface with a single platform.

Search Breach Data Without Limits
Run unlimited, high-speed queries across HEROIC’s global breach intelligence database including emails, usernames, domains, phone numbers, IPs, and other identity types.

Engineered for enterprise visiblity and rapid response
Get direct access to verified breach data and compromised credentials with HEROIC DarkWatch: The platform that empowers enterprises to detect exposure early, prioritize high-risk events, and take immediate action, without wasting time on noise or outdated data.
Think your company credentials are safe? Let’s find out.
One search can change your entire threat picture. Scan our database for free.
Key Features
With over 400 billion records and growing, Darkhive delivers the most comprehensive and actionable breach data available, all under one roof.
Access the worlds largest database of breached credentials.
Get instant access to billions of exposed credentials collected from breaches, stealer logs, and underground sources. Continuously updated and deduplicated, this unmatched dataset helps you uncover compromised identities across your organization, reduce risk at scale, and stay ahead of threats long before they become incidents.
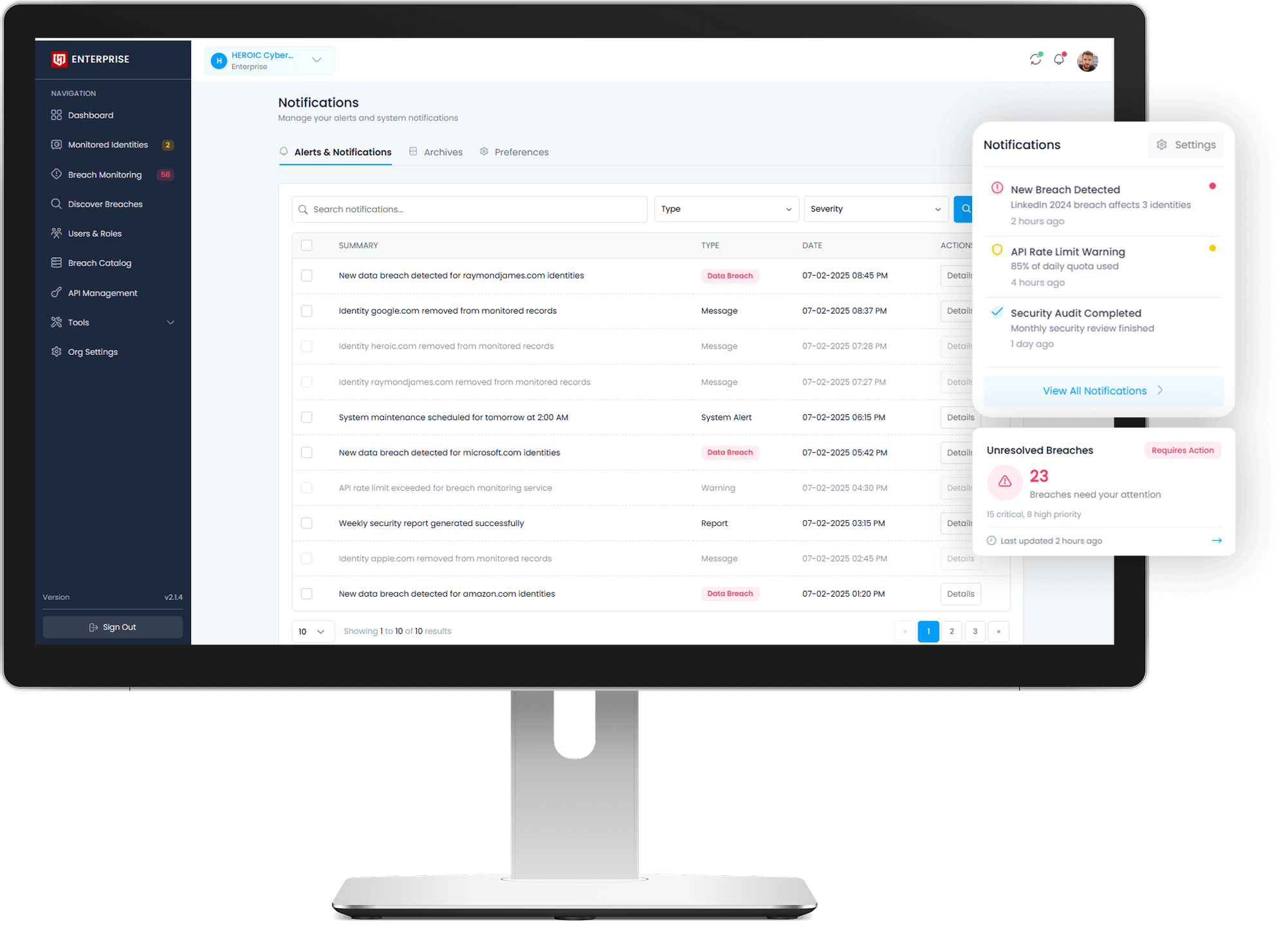
Explore All Breaches

High-Fidelity Breach Alerts and Breach Resolution
Not all breach data is useful, and frankly most of it is noise. Darkwatch delivers verified, context-rich alerts tied to real, actionable identity threats. Each alert includes exposure timelines, source details, and mapped identity types, helping your team focus on what matters without wasting time on false positives.
Multi-Identity Coverage
Modern identity threats don’t stop at email addresses. Darkwatch supports full-spectrum monitoring across emails, usernames, domains, IPs, phone numbers, SSNs, and more, enabling visibility and response for employees, third parties, customers, and executive accounts alike.
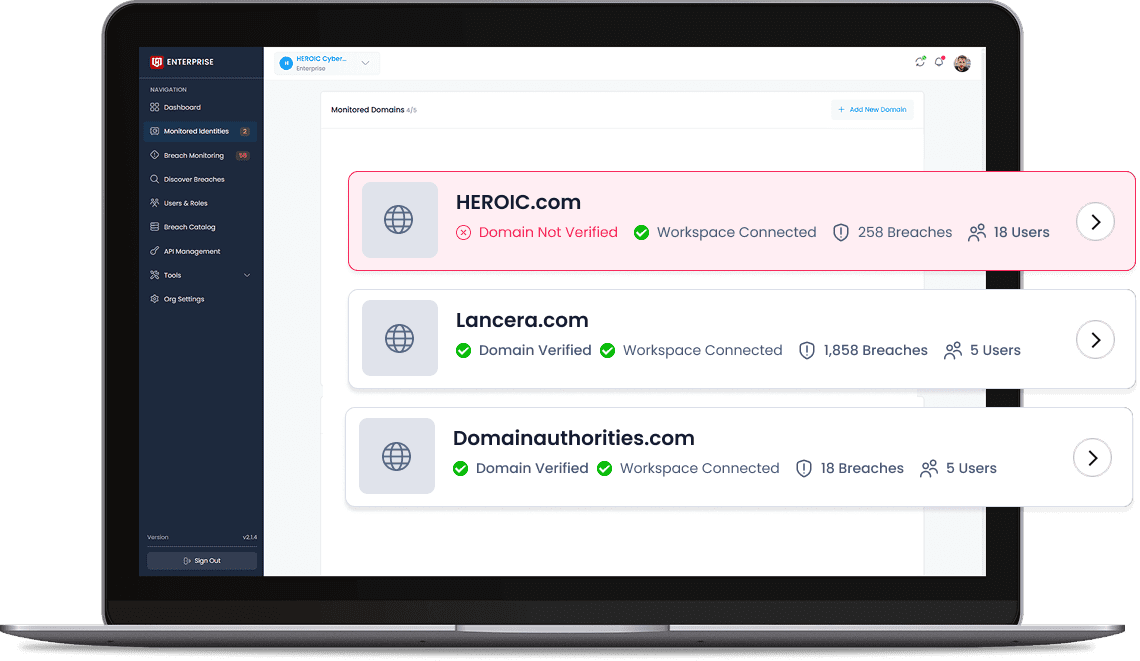
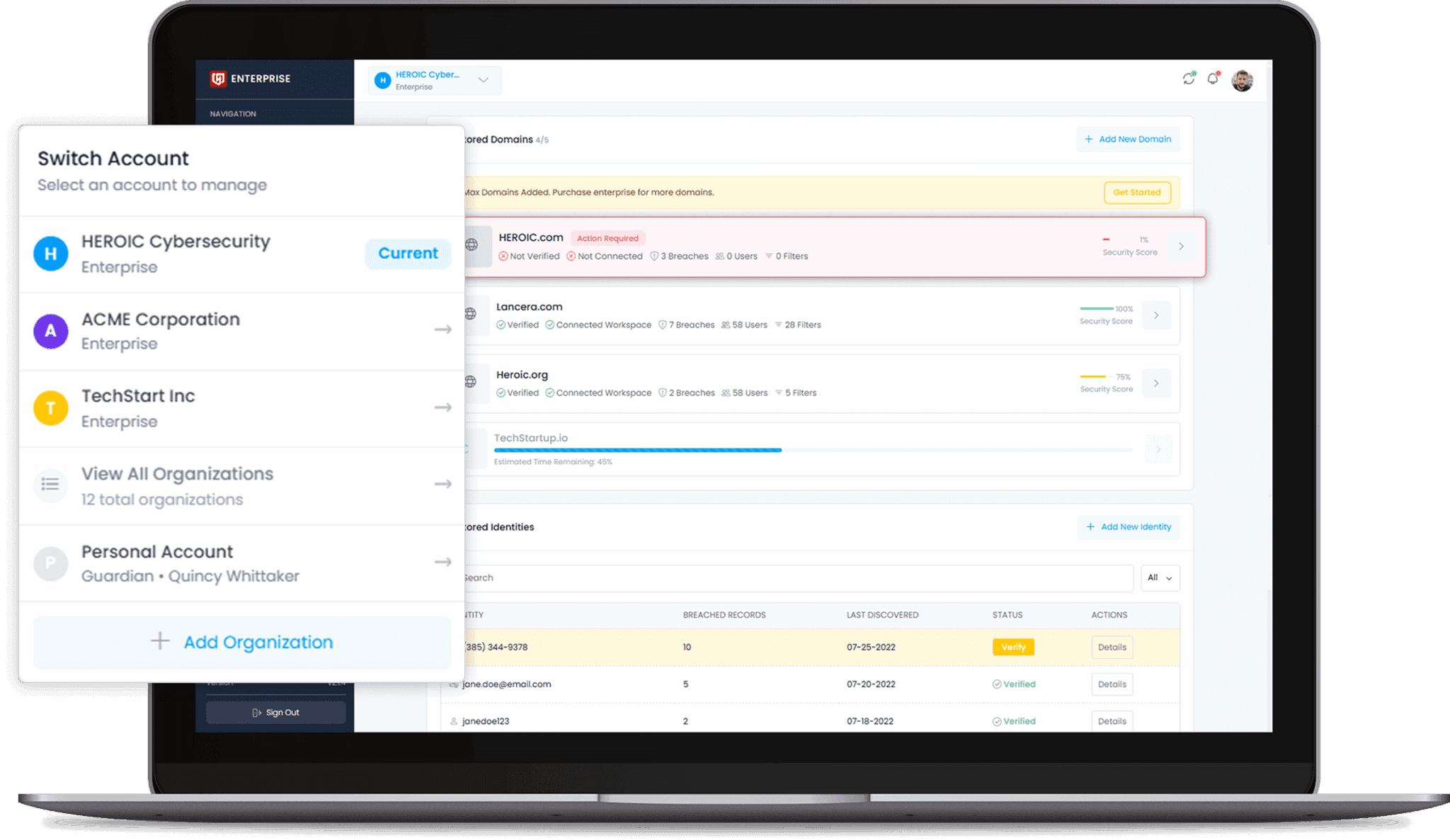
Flexibile Multi-Organization Management and team users.
Enterprise threat intelligence for companies
With over 400 billion records and growing, Darkhive delivers the most comprehensive and actionable breach data available, all under one roof.
Stop Guessing. Start Seeing.
Get verified breach intelligence before attackers do — and take action while others are still reacting.
Get a Demo and See the Real Threats affecting your company (or clients).
Phone
1-800-613-8582
sales@heroic.com
Monday – Friday // 8:00am – 5:00PM MST













/includes/qr-code.png)