Instantly Search the Dark Web for Your Exposed Data
We collect, analyze, and find data from the darkest corners of the internet
Every day, millions of new records are stolen through breaches, malware infections, and stealer logs and quietly traded in dark-web markets long before victims ever find out.
Your credentials, personal information, or business data could already be circulating, even if you’ve never been “officially” breached.

The Cost of Exposure
%
Of people never realize their data was exposed until it's been used.
Active users has data circulating in multiple breach datasets.
%
Of cyberattacks start with stolen credentials.
From the Dark Web to Your Dashboard
Building for the Age of AI
We turn raw, chaotic breach data into structured intelligence that anyone can understand.
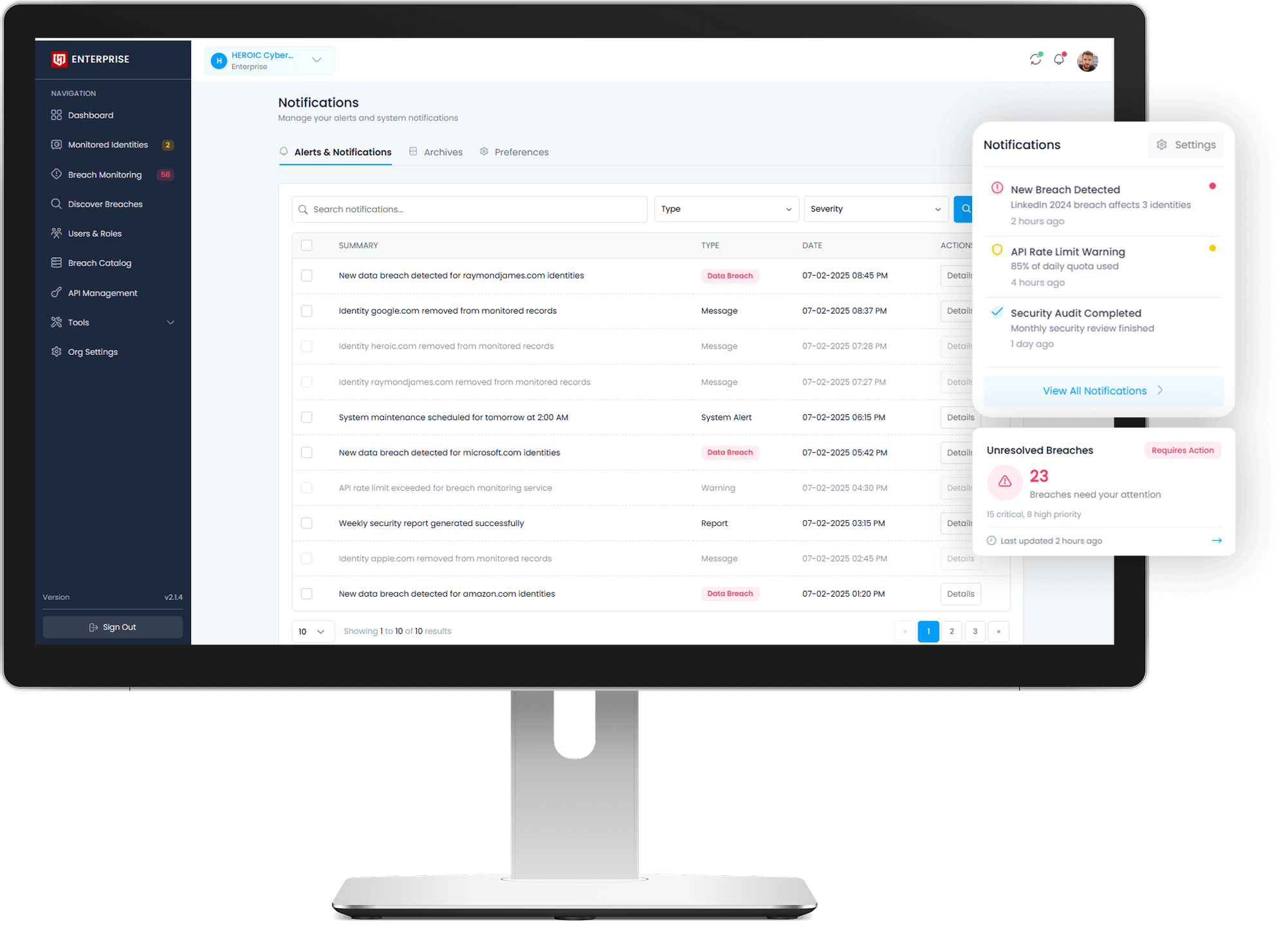

HEROIC finds over 400+ million breaches every month.
Billions of stolen records are actively circulating across known breach datasets and that number continues to climb daily.
Most of this information has been sold, merged, or reposted countless times, increasing visibility with every transaction. Once a single database is leaked, the data never disappears, it becomes a permanent part of the underground economy.
Our intelligence network monitors and analyzes data from the deepest layers of the internet to uncover real exposures before they spread.

Dark-Web Forums and Marketplaces
Primary hubs for trading stolen databases, credentials, and sensitive information among cybercriminal groups.

Malware and Stealer-Log Collections

Public and Private Breach Disclosures

Underground Telegram and Discord Channels

Paste Sites and Leak Hubs

Deep-Web Sources
Help Us Redefine Cybersecurity
Explore open positions and be part of building a safer digital world.
Join the Mission
Cybersecurity is entering a new era one defined by intelligence, collaboration, and adaptability.
HEROIC is where that future is being built.

/includes/qr-code.png)