HEROIC API™
Access Darkhive Data Directly from the HEROIC API
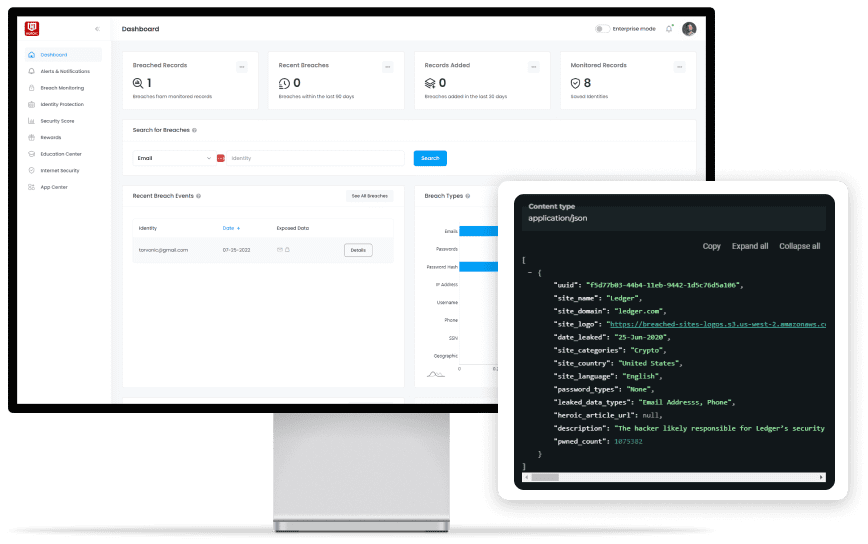
Integrate darkhive into your existing product

YOUR COMPANY
Software, Service, or Database

Darkhive Breach Model
Data holds no value unless it’s actionable. Our database will show email addresses, passwords (including hashes), usernames, IP addresses and any other information that may have been exposed for your team to properly remediate.
Blazing Fast Searches
Custom Data Delivery
Private Server Cluster and API Endpoints
Over 400 Billion+ Breached Records From The Dark Web

Data is breached and then leaked online

hEROIC UNCOVERS THE DATA AS IT’S SHARED

DATA IS CLEANED, Processed, & distributed
HOW IT WORKS


/includes/qr-code.png)