Cybernews has confirmed the 16 billion passwords breach,
The cybersecurity landscape is grappling with what experts are now calling the largest credential exposure event on record. A trove of over 30 newly surfaced databases, primarily sourced from advanced infostealer malware such as RedLine, Raccoon, Vidar, and Lumma, includes billions of plaintext records containing login credentials, browser session tokens, and sensitive metadata. These datasets were briefly hosted on misconfigured Elasticsearch clusters and unsecured object storage buckets (S3-compatible), allowing researchers to intercept portions of the leak before takedown or encryption by threat actors.
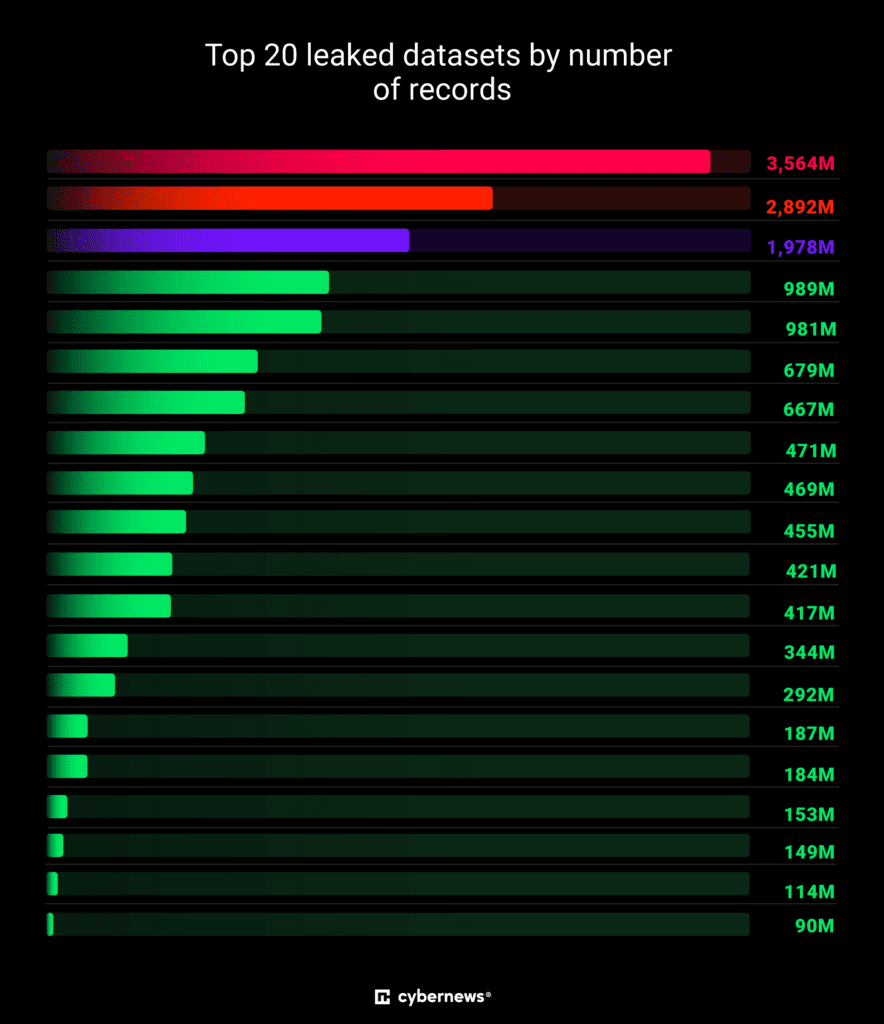
Photo Credit: https://cybernews.com/
Researchers began monitoring this surge early in the year and have already logged collections ranging from 16 million to more than 3.5 billion records each. New mega-dumps appear every few weeks, proving that infostealer campaigns are accelerating rather than fading. Because the data briefly sat on misconfigured Elasticsearch and public object-storage servers, investigators captured evidence before the caches vanished, yet they could not determine who controls the troves. Aggregated datasets of this size are prized for phishing, ransomware deployment and business email compromise, making the largest credential leak a powerful engine for mass exploitation.
🔍 Sizes of Detected Dumps:
Collections vary from 16 million records to over 3.5 billion records each, with cumulative estimates exceeding 16 billion leaked credentials as of Q2 2025.
[Sources: Hudson Rock, Cybernews, Heroic DarkWatch, SOCRadar]
The danger lies in the structure of the leak. Each row supplies everything needed for immediate account takeover and can bypass simple password resets if a service fails to invalidate stolen cookies or tokens. Even a one-percent success rate would hand threat actors millions of footholds for identity theft, espionage and targeted scams.
Defense starts with fundamentals. Replace reused passwords with unique, complex phrases generated by a manager. Activate multi-factor authentication across every service and verify that sessions are revoked after password changes. Run endpoint scans to evict infostealer malware and audit browser extensions that capture credentials. Continuous monitoring of account activity and swift response to anomalies remain critical as the fallout from the 16 billion passwords breach unfolds.
Structural Risk: Not Just Passwords
What sets this leak apart is its completeness. Many entries contain active session cookies and OAuth tokens, enabling attackers to bypass traditional defenses like password resets, especially where session revocation is poorly implemented.
This aligns with the MITRE ATT&CK techniques:

Photo Credit: https://cybernews.com/

Photo Credit: https://cybernews.com/

Photo Credit: https://cybernews.com/
-
T1556.001: Steal Web Session Cookie -
T1078: Valid Accounts -
T1555: Credentials from Password Stores
Even if only 1% of credentials remain valid, that still presents 160 million viable entry points across digital ecosystems.
Get HEROIC Guardian now! Stay ahead of cyber threats with real-time breach monitoring. Guardian scans the dark web to identify when your data has been leaked, providing instant details about the exposure. From compromised passwords to sensitive information, our platform empowers you to act swiftly and mitigate risks before they escalate.
Click here to learn more: https://heroic.com/products/guardian/





/includes/qr-code.png)