HEROIC DARKWATCH™
Real-time visibility into compromised identities, credential leaks, and breach activity across the web.
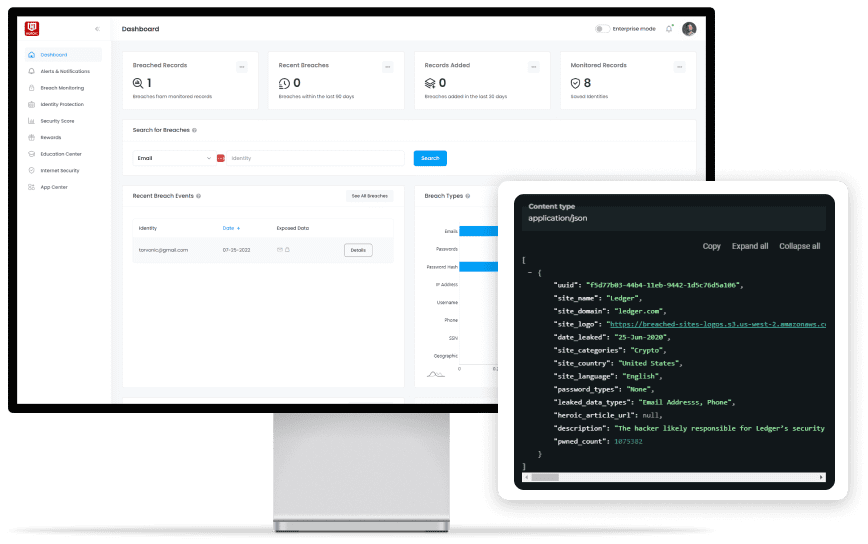
Stop Guessing. Start Seeing.
Get verified breach intelligence before attackers do — and take action while others are still reacting.
Key Features
With over 400 billion records and growing, Darkhive delivers the most comprehensive and actionable breach data available, all under one roof.

Detect Identity Threats Instantly
Continuously monitor the open, deep, and dark web for compromised credentials, stealer logs, and exposed identity data the moment it surfaces.

Filter Noise with Precision
Cut through the flood of breach data using advanced deduplication, intelligent correlation, and automated filtering that highlights only verified, high-impact threats.

Integrate Seamlessly Into Your Stack
Connect breach intelligence into your SIEM, SOAR, IAM, and other tools via robust APIs — accelerating deployment without disrupting your existing workflows.

Detect Identity Threats Instantly
Continuously monitor the open, deep, and dark web for compromised credentials, stealer logs, and exposed identity data the moment it surfaces.

Filter Noise with Precision
Cut through the flood of breach data using advanced deduplication, intelligent correlation, and automated filtering that highlights only verified, high-impact threats.

Integrate Seamlessly Into Your Stack
Connect breach intelligence into your SIEM, SOAR, IAM, and other tools via robust APIs — accelerating deployment without disrupting your existing workflows.
Smarter Threat Data for Smarter Response
With over 400 billion records and growing, Darkhive delivers the most comprehensive and actionable breach data available, all under one roof.
Real-Time Identity Threat Detection
Explore All Breaches
High-Fidelity Breach Alerts

Advanced Deduplication & Filtering
Multi-Identity Coverage
Seamless Integration with Existing Systems
Built with interoperability in mind, Darkwatch plugs directly into your existing SIEM, SOAR, IAM, EDR, and ticketing systems. Our robust APIs and standardized data structures ensure fast deployment, reduced complexity, and immediate value without disrupting existing workflows.
Risk Scoring & Threat Context
Each breach event is enriched with contextual intelligence, from breach origin and timestamp to password reuse indicators and known threat actor behavior. Darkwatch’s risk scoring engine helps your team triage efficiently and prioritize the most critical threats first.
Stop Guessing. Start Seeing.
Get verified breach intelligence before attackers do — and take action while others are still reacting.
Get a Demo and See the Real Threats affecting your company (or clients).
Phone
1-800-613-8582
sales@heroic.com
Monday – Friday // 8:00am – 5:00PM MST












/includes/qr-code.png)