The Basics of Cybersecurity
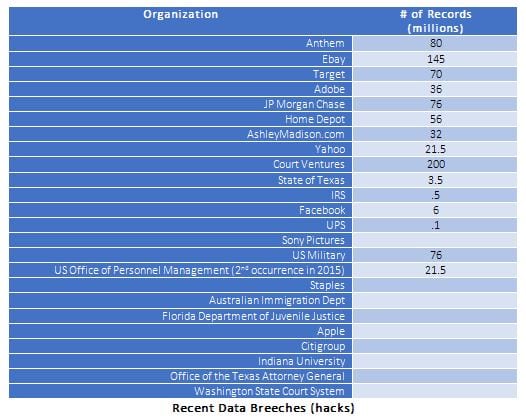
The news these days seems to be replete each week with stories of additional companies falling victim to being “hacked”, with their internal information being damaged or stolen. In fact, in the past two years, millions of personal records have been stolen from organizations such as Anthem Health (80 Million), eBay (145 Million), Target (70 Million), JP Morgan (76 Million), Home Depot (56 Million), Court Ventures (200 Million) and even the IRS, US Military, and US Office of Personnel Management (twice in 2015).
For those of us who are not all that familiar with computer jargon, we only know this isn’t a good thing, but don’t really understand how this could impact us and our families. Unfortunately the fact is that hacking affects many individual’s not just large organizations, and many experts feel it is only a matter of time before most people are hacked.
What is hacking?
Governments, military, corporations, financial institutions, hospitals and other businesses collect, process and store a great deal of confidential information on computers and transmit that data across networks to other computers. “Hacking” is the process of using a computer to gain unauthorized access to data on a computer or in a system, such as a medical or banking systems. With information such as names, social security numbers, addresses, fingerprints, banking information, medical information, financial history and other private details, it is easy to steal people’s identities and conduct other illegal activities.
The government has also become concerned with the sophisticated hacking being conducted by terrorist groups and foreign governments called “cyberterrorism”, which can affect financial and infrastructure systems (electricity, water, transportation) in the U.S. During a Senate hearing in March 2013, the nation’s top intelligence officials warned that cyber-attacks and digital spying are the top threat to national security, eclipsing terrorism. With the growing volume and sophistication of hacking and cyberterrorism, more attention is needed to protect both business and personal information, as well as safeguard national security.
Cybersecurity
In order to combat hacking and data theft, organizations have hired specialized people that focus on “cyber security”, which is the process of protecting computers, networks, programs and data from unauthorized access, theft or destruction. Although these people use sophisticated methods to protect the company’s information, there are still a number of actions that we as individuals can take to protect the personal information located in our computers, and in our home networks.
Here are 5 key recommendations to ensure your personal information is secure:
1. Backup Your Files:
Backup (copy) your files (tax returns, documents, photo’s, etc) onto a portable hard drive, CD ROM, or a cloud based secure service (HEROIC.com) to protect against theft and/or damage.
2. Fight against malware:
Malware, short for malicious software, is software designed to attack computer operations, gather sensitive information, or gain unauthorized access to computer data.
Get a good Malware scanner/removal program: There are many reputable Malware programs available on the market. Also, some computer support and cyber security companies (HEROIC.com) can clean Malware, and install and support malware scanning programs.
- Don’t fall for offers that look too good to be true: If you receive an offer that you just can’t pass up, let it go. It may be someone trying to access your system and steal your information. Never click on an email link from someone or a company that you don’t know. They could include “malware” that can allow hackers into your computer.
- Email Scams: If you receive an “odd” email from someone you know contact that person BEFORE you open it to make sure the email is legit. Again, don’t click on email links from people or companies you don’t know. Also, DON’T forward emails from others to your friends and family without first checking them with a registered malware scanner. If these contain malware or viruses you will be allowing hackers into their computer in addition to your own.
The “United States Computer Emergency Readiness Team (US-CERT)” provides information for recognizing and avoiding email scams. www.us-cert.gov.
3. Wi-Fi Security:
Most homes have a Wi-Fi network these days to connect computers to the internet, support smart phones, for TV (Roku, Netflix), and for gaming consoles and security systems.
Wi-Fi Routers are boxes that most likely sit near your computer and can be identified by the internet connections and wireless antennas attached. These have internal security features that must be activated to help prevent unauthorized access to your home network/computer. Contact a specialist to make sure you have the appropriate security enabled.
4. Secure Your Web Browser:
Web browsers (Internet Explorer, Google Chrome, Firefox, etc) can allow harmful malware and viruses into your computer. Make sure you have a professional enable your computers “firewall”, which helps secure your computer and data, and also use a “pop-up” blocker, normally included in your browser settings.
5. Mobile Security:
A new area of concern is related to the use of Smart Phones and Tablet Computers, otherwise known as “Mobile Devices”. These devices can be compromised through specialized viruses and malware, allowing hacker’s entry into the device.
Most smartphones and tablets are connected to your home Wi-Fi and therefore if the hackers get into your Mobile device, they can gain access to your personal computer. Specialized security programs and settings are available for your Mobile devices. We recommend speaking to your phone provider, or a professional cyber security provider to ensure these devices are secure.
With a little effort your personal information and computer can be secure online. Of course hackers will continuously be working to defeat any security measures you put in place, and as such it is important to keep your systems security up to date. If you are unsure how to do this, we recommend you hire a reputable security service to provide that support. The advantage in a professional organization is that they can apply their people and skills to continually upgrade systems and defeat possible threats, removing the worry for those of us that don’t have those skills or resources.
Has Your Email Account Been Hacked?
See if your email has been compromised with the most powerful scan engine.
 All information submitted is 100% Private and Secure.
All information submitted is 100% Private and Secure.