Has Your Email Been Compromised?
Check and see if your email has been involved in a databreach
 All information submitted is Private and Secure. We do not sell or share email addresses.
All information submitted is Private and Secure. We do not sell or share email addresses. 
BreachForums TXTLogCloud 15M ULP by phiso7777
On November 10, 2024, a stealer log named 15M FREE LINES | @txtlogcloudd surfaced on a well-known hacking forum. The post references "leeched from t.me/txtlogcloudd" and includes 15,000,000 user records. Out of the total records, 2,192,000 are unique. The data exposed consists of email addresses, URLs, and plaintext passwords. This incident underscores the critical importance of robust cybersecurity measures, as exposure of such personal information can have significant privacy implications.

LeakBase 140M+ ULP by FFish
On October 19, 2024, a stealer log named 140Million+ Url Logın Pass surfaced on a well-known hacking forum. The post references "Mixed URL LOGIN PASS 3.44GB compressed 9.64GB uncompressed" and includes more than 140,000,000 user records. Out of the total records, 12,620,000 are unique. The data exposed consists of email addresses, URLs, and plaintext passwords. This incident underscores the critical importance of robust cybersecurity measures, as exposure of such personal information can have significant privacy implications.

Vietloan
On February 23, 2024, the Vietnamese online platform offering loan services Vietloan suffered a data breach and compromised 2.1 million unique email addresses, along with names, phone numbers, gender, and date of birth. This incident highlights the crucial importance of maintaining high cybersecurity standards to protect sensitive personal and financial information.

MuMaYi
In May 2011, the Chinese Android site MuMaYi experienced a data breach affecting 132,000 subscribers. The compromised data included email addresses, IP addresses, usernames, dates of birth, and passwords stored as MD5 hashes. This incident underscores the importance of implementing robust cybersecurity measures, as using outdated encryption like MD5 can leave sensitive data vulnerable to unauthorized access. Strong security protocols are essential to protect user privacy and maintain trust.

LeakBase 4,3Kk ULP by firegoon
Around May 6, 2024, a stealer log named 4,3Kk Url:log:pass surfaced on a well-known hacking forum. The post does not have any references but includes approximately 4,300,000 records. Out of the total records, 809,042 are unique. The data exposed consists of email addresses, URLs, and plaintext passwords. This incident underscores the critical importance of robust cybersecurity measures, as exposure to such personal information can have significant privacy implications.

Lako do posla
In July 2022, the job recruitment platform Lako do posla experienced a data breach affecting 517,000 users. The compromised information included email addresses, full names, phone numbers, physical addresses, genders, birthdays, and passwords stored as Bcrypt hashes and plain text. This incident emphasizes the importance of robust cybersecurity measures in protecting user information.

Kixify
In September 2023, a significant data breach affected Kixify, popular sneaker marketplace, compromising over 850,000 unique records. Exposed information included email addresses, names, usernames, phone numbers, and personal addresses, all accessed via an unsecured admin panel. This highlights the critical need for securing administrative access to prevent unauthorized data exposure.

LOL Hentai
In January 2021, the adult content site LOL Hentai, focused on League of Legends-themed material, suffered a data breach affecting 84,600 members. Exposed information included usernames, email addresses, and passwords stored using MD5 hashing. This highlights the critical need for secure password storage practices and comprehensive cybersecurity protocols.

LeakBase 10Kk ULP Part 3 by firegoon
On February 18, 2024, a stealer log titled 10Kk ULP Part 3 was shared on a prominent hacking forum, comprising approximately 10 million records. The exposed data included nearly 1.7 million unique email addresses, plaintext passwords, and homepage URLs. This breach demonstrates the persistent threat posed by stealer malware and highlights the necessity of proactive cybersecurity practices, such as regularly updating software and utilizing strong, unique passwords.

LeakBase 10Kk ULP Part 1 by firegoon
On February 18, 2024, a stealer log titled 10Kk ULP Part 1 was uploaded to a prominent hacking forum, containing approximately 10 million records. The compromised data included around 800,000 unique email addresses, plaintext passwords, and homepage URLs. This incident highlights the ongoing risks posed by stealer malware and underscores the importance of robust cybersecurity measures, such as password management and multi-factor authentication, to safeguard sensitive information.

MyPirata
In December 2019, the now-defunct anime forum MyPirata experienced a data breach affecting 503,000 members. The compromised information included usernames, email addresses, IP addresses, and passwords stored as MD5 hashes. This incident underscores the critical need for robust cybersecurity measures, as relying on outdated encryption methods like MD5 makes sensitive data more vulnerable to unauthorized access. Implementing stronger security protocols is essential to protect user data and maintain privacy.

LeakBase 8Kk ULP by FobiBoom
On March 13, 2024, a stealer log titled 8Kk Url:login:pass was posted on a prominent hacking forum. The log contained approximately 8 million records, revealing 1.1 million unique email addresses, plaintext passwords, and homepage URLs. This incident highlights the ongoing threats posed by stolen credential dumps and the need for robust cybersecurity measures to mitigate such risks.

TEG
In June 2024, TEG, a leading entertainment and ticketing service provider in Australia, experienced a data breach that impacted nearly 30 million users. The exposed data included approx 17.5 million email addresses, names, phone numbers, dates of birth, usernames, and password hashes. This breach underscores the critical need for robust cybersecurity measures to protect sensitive personal information and mitigate the risks of unauthorized access and data misuse.

LeakBase 10Kk ULP by firme12
On October 8, 2024, a stealer log named 10Kk (Não É Meu) surfaced on a well-known hacking forum. The post references "aproveita" and includes 10,000,000 user records. Out of the total records, 3,221,000 are unique. The data exposed consists of email addresses, URLs, and plaintext passwords. This incident underscores the critical importance of robust cybersecurity measures, as exposure to such personal information can have significant privacy implications.

Muscle Nutrition
In September 2022, the Italian webstore Muscle Nutrition experienced a data breach affecting 138,000 users. The exposed data included email addresses, full names, physical addresses, and passwords stored as either MD5 or bcrypt hashes. The breach reportedly occurred due to factors such as Google dorking, server misconfiguration, database panel vulnerabilities, and easily guessable credentials. This incident highlights the importance of robust cybersecurity measures, as weaknesses in server and access configurations can expose sensitive user information. Implementing strong security protocols and regular system audits are essential to prevent such vulnerabilities and protect user data.

LeakBase 1.19Kk ULP by blockchair
On October 19, 2024, a stealer log named 1.1Kk Ulp From Logs surfaced on a well-known hacking forum. The post references "Pulled from the logs 15.10" and includes 1,190,000 user records. Out of the total records, 140,240 are unique. The data exposed consists of email addresses, URLs, and plaintext passwords. This incident underscores the critical importance of robust cybersecurity measures, as exposure to such personal information can have significant privacy implications.

MOVEit
In May 2023, a critical vulnerability in the MOVEit file transfer service was discovered, compromising sensitive information for thousands of organizations worldwide. On November 11, 2024, a threat actor known as Nam3L3ss began publicly releasing this data, which includes detailed employee records from 25 major companies and organizations. Among those affected are tech giants like Amazon, Lenovo, and HP; banks such as U.S. Bank and Union Bank of Switzerland; and other major corporations like McDonald’s and Delta Airlines. In total, over 5.8 million records were exposed, containing full names, email addresses, phone numbers, work addresses, and organizational structures. This breach underscores the importance of rigorous cybersecurity practices to protect against the risks of data exploitation.

LeakBase 24Kk ULP part 1 by firegoon
On March 22, 2024, a stealer log titled 24Kk Url:log:pass was posted on a prominent hacking forum. The log contained approximately 24 million records, revealing 2.2 million unique email addresses, plaintext passwords, and homepage URLs. This incident highlights the ongoing threats posed by stolen credential dumps and the need for robust cybersecurity measures to mitigate such risks.

DemandScience (Pure Incubation)
In February 2024, a substantial dataset from DemandScience, a subsidiary of Pure Incubation, was listed for sale on a well-known hacking forum. This breach, later traced back to a retired legacy system, primarily consisted of business contact information that had largely been compiled from public sources. The exposed data encompassed total of 132.5 million records and approx 125 million unique corporate email addresses, as well as physical addresses, phone numbers, employers, and job titles. This incident underscores the importance of stringent data management and secure decommissioning practices to protect business and personal information from exposure.

Cracked 30M ULP by Yeetizy
On July 26, 2024, a stealer log titled 30M ULP was shared on a prominent hacking forum. The log comprised approximately 30 million records, including a collection of around 1.7 million unique email addresses, plaintext passwords, and URL links. This incident underscores the necessity of implementing strong cybersecurity practices to protect sensitive data and mitigate the risks posed by such breaches.
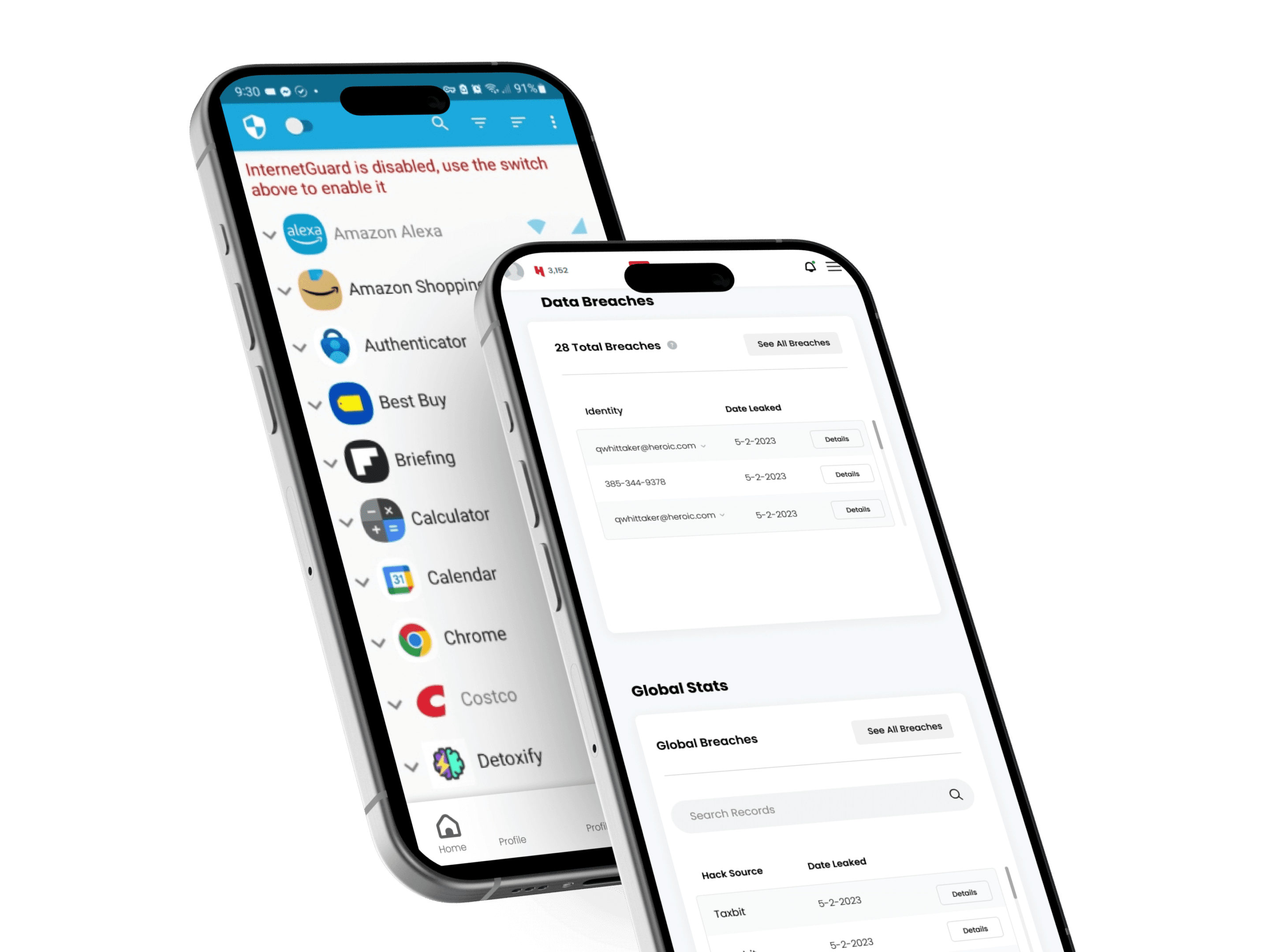
Unique fingerprints of over 5 billion email addresses
The Worlds Largest Breach Database
Over 5 Billion Records
Our Data Collection Process
Our lives rely on technology. We use it to do our jobs, entertain ourselves and stay connected. As technology continues to grow, our reliance on that technology does as well.

An organization’s employee and/or customer databases are either stolen or leaked by a malicious party

The compromised data is placed on the dark web where malicious threats and attackers obtain the data

HEROIC threat analysts discover the leaked and compromised data in hacker forums, paste bins, etc.

The data is then verified, cleaned and uploaded into HEROIC DarkHive™ for search and reporting

Users and organizations using HEROIC receive account alerts and other remediation actions

