How Hackers Can Take Over Your Home Computer
Have you ever wondered how hackers can take over their victims’ computers? Have you wondered what a hacker would want once they’re inside? Sophie Curtis, journalist for The Telegraph newspaper out of Great Britain volunteered to have her computer hacked. She quickly found out how easily her most sensitive and personal information can become vulnerable to cyber criminals.
%
Percent of computers that are vulnerable to hacker exploit kits.
Average number of months that a cybersecurity breach goes unnoticed.
%
Percent of Americans who have been victims of cyber crime.
Whether you’re a nation or a citizen, cyber security is an ever-growing issue – new hacks or data breaches emerge daily, in which people’s information is exposed or leaked, from bank details to intimate photographs. But is the threat of being hacked something that you or I really need to worry about? And if someone did hack into your computer, what would they be able to do with the information they found?
Over the summer I decided to put these questions to the test. I got in touch with an ‘ethical hacker’ called John Yeo, who works for cyber security firm Trustwave, and asked him to try and hack me.
The job of an ethical hacker is to do ‘penetration testing’ for companies. This means they adopt the role of a real hacker and use the same tools that real hackers use to try and break into a company’s computer systems, to identify vulnerabilities. The ethical hacker then tells the company what they have found, so that it can fix the vulnerabilities before a real hacker discovers and exploits them.
Hacking an individual is quite a different matter, and John warned me that the attempt may be unsuccessful. Apart from anything else, I knew that it was coming, so would inevitably be more cautious than usual about opening suspicious emails. He also explained that most hackers would ‘spread their bets’ and target large numbers of people in one go, rather than just one, to increase their chances of success. However, he said he would give it a go.
On 24 July I signed a waiver stating that the ethical hacking would be carried out at my own risk and that I would be solely responsible for any damage. Then everything went very quiet. I went about my life as normal, and John and his team of ethical hackers at Trustwave ‘SpiderLabs’ began scraping the internet for every piece of information they could about me.
This meant identifying every social networking account, every email account and every online service I had ever signed up to. No attempts were made to break into any of these accounts initially, simply to lift as much information as possible to try and build up a profile of who I was.
Having written a fair amount about cyber security over the past few years, I’m pleased to say that most of my profiles are fairly locked-down. My Facebook has particularly high security settings – almost nothing is visible to anyone who is not an approved friend, and no one who is not at least a friend-of-a-friend is able to send me a request.
This meant that the hackers had little hope of getting to me directly that way. The most they were able to discover was the names of my family members and my fiance, as well as my school, my university and the companies I have worked for in the past.
But they then used a popular family tree history website to verify my birth details, including birth date, mother’s name, father’s name, and my full name. They also discovered that an ancestor of my mother – a former Attorney General – had been a peer.
They were able to use Twitter to find out my work email address, as well as some of my recent locations and the name of a regular social night I attend with other journalists. From objects in the background of one of the photos I had posted on Twitter they were able to discover what mobile phone I used to use, and the fact that my fiance used to smoke roll-ups (it was an old photo), as well as the fact he likes cycling.
While these details may seem inconsequential, they all helped the hackers to build up a picture of who I am, so that when it came to launching a targeted attack, they could make it as personal as possible.
The first time the ethical hackers attempted to make direct contact with me was on 9 September. I received an email from an account named ‘Ricardo Almeida’, requesting a meeting later in the week. As there was no context to the request I ignored it; approaching a journalist in such a way, however, is particularly likely to be successful.
Nonetheless, I later found out that the email contained a tiny image (just one pixel by one pixel). This was the hackers’ first attempt to ‘fingerprint’ my computer. The aim of this is to identify which operating system the computer is running, as well as which browser I was using, which browser add-ons I had, and which security software might be running on the computer.
Normally, when an email contains an image, the receiver’s email client has to contact the sender’s email server in order to ‘fetch’ the image. This is when the hackers would have been able to fingerprint the computer. However, Gmail works differently, in that it ‘prefetches’ the image, meaning it is Google that contacts the sender’s email server and retrieves the image rather than the receiver’s computer. The attempt was therefore unsuccessful.
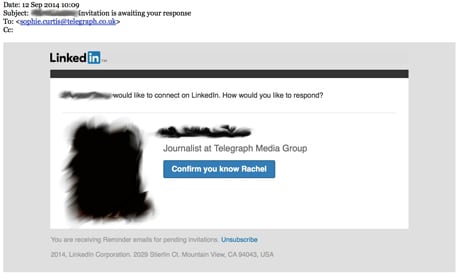
The next attempt was on 12 September. This time the hackers created an email that appeared to be a request from another Telegraph journalist to connect on LinkedIn:
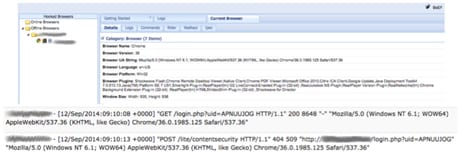
I admit that LinkedIn is the one social network on which I do accept requests even if I do not know the person. Without thinking I clicked the ‘confirm you know Rachel’ button. I don’t, because she doesn’t exist. I behaved just the same way millions do every day. The request was sent back to the hackers and they had fingerprinted my computer:
I later discovered that even if I had pressed ‘Unsubscribe’ they would have been able to fingerprint my computer in the same way. All I had to do was interact with the email.
The ethical hackers were now ready to launch their attack. They had gathered as much information as they could about me from public sources, and they had a profile of my computer, so they knew how to construct the malware which would later infect it.
Knowing what they knew, they could have gone down the personal route, using information about my family or fiance to target me. Instead they decided to appeal to my journalistic instincts.
They constructed an email, which I received on 30 September, in which they claimed to be members of a worldwide activist group, which had obtained confidential files from the UK government. They said they were working with national newspapers from the USA, Germany, Italy, France, Brazil, Argentina and South Africa to leak the document, and invited me to be a primary channel for public disclosure on behalf of The Telegraph.
They referred back to the email from Ricardo Almeida, claiming that this had been an alias for one of their local collaborators. They also said that the documents would be released on 3 October 2014, creating a sense of urgency.
They said they had attached a “partial extract” of the document, which was compressed and encrypted with a strong password “in order to reduce the file size and increase the security of their communication”. They added that, if I agreed to publish an article “in accordance with their coordinated global release date”, they would send me the full document and related files.
The attached document appeared to be a .rar file, which required me to download a tool called WinRAR to extract the file. They also included brief instructions for downloading the file on a Windows PC.
When I received the email alarm bells started ringing. The story seemed a bit far-fetched, and the fact that it was a .rar file made me suspicious. However, the sender’s emphasis on the need for security seemed to tally with what I’ve heard about whistleblowers in the past, and a large part of me thought that if it was real and I ignored it, I would never live it down.
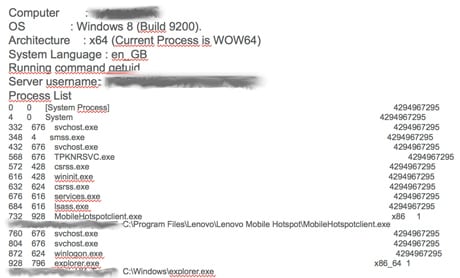
I decided to try opening the attachment on my laptop at home rather than risk any hackers getting onto the Telegraph’s corporate network. When I got home that night I downloaded WinRAR (a perfectly legitimate program) on my Windows laptop and downloaded the attachment. When I attempted to open the attachment it didn’t appear to open, but it was too late – they were in, and they had planted a ‘remote access trojan’ on my computer:
Windows Defender on my laptop went a bit berserk at this point and started popping up with lots of error messages. Of course I realised what had happened and ran a virus scan. A couple of files were flagged up, which I deleted, but this didn’t make any difference.
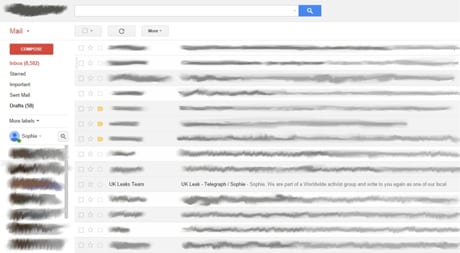
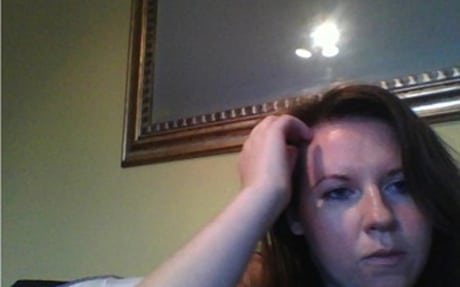
In order to prove they had got in, the hackers took a screenshot of my Gmail account, which was open on my desktop at the time:
They also turned on my webcam and took this particularly attractive photo of me:
By now, the hackers had complete administrative control of my laptop. They were not only able to see everything I did on the computer, but also control the computer themselves – open up applications, browsers, download cookies, control the camera and microphone and all manner of other things.
Because they are ethical hackers, they stopped at this point – they had proved their point. But for a real hacker, this would be just be the beginning. They could stay tapped into my computer for days or weeks, watching everything I did; they could install a keylogger and record every password I typed into every website I visited; they could go through my emails and lift out copies of my passport that I sent to my solicitor when buying a flat last year; they could watch as I connected to my work computer over the network and look at files I had stored there.
Even if I restarted my computer (which I did), the malware they had installed on it would call back to the hackers’ systems as soon as I turned it on again, giving them full remote access control once again.
Needless to say, I was feeling pretty stupid by the time I met up with John again this week. He talked me through everything they had done. Perhaps most frighteningly, he reassured me that, as targets go, I was a pretty tough one to crack.
In most cases, he said, the hackers would have been able to gather a lot more personal information about their target in the early stages, by lifting data from social networks. They were not able to get hold of either of my personal email addresses – only my work email, which I have shared with people on Twitter – and were not able to get near my Facebook account, where the vast majority of my personal information is stored.
But that doesn’t change the fact that I – someone who should know better – was hacked. It’s a salutary tale, mitigated only slightly by the fact that it’s apparently something that could happen to all of us, with precious little that can really be done to prevent it.
Sophie’s experience should be eye-opening to all of us. Our best attempts at using the Internet safely is not enough to defend ourselves from hackers. Don’t THINK you’re safe from hackers, KNOW you are with HEROIC.
Has Your Email Account Been Hacked?
See if your email has been compromised with the most powerful scan engine.
 All information submitted is 100% Private and Secure.
All information submitted is 100% Private and Secure.