Credential Stuffing: The Threat Your Company Should Be Watching
Credential stuffing is a popular method of cyber attack that may be affecting your company without you ever being aware of it. As the culprit of large data hacks, like Yahoo, who won the title of both being victim of the first and second largest credential spills ever reported, credential stuffing is something no company should close a blind eye to. So, what exactly is credential stuffing and why is it relevant to your company?
What Is Credential Stuffing?
Credential stuffing is a type of cyber attack where hackers run numerous stolen login credentials against a targeted website in an attempt to gain access to online accounts. In simple terms, credential stuffing is when a large number of emails, usernames and passwords are entered into websites until the attacking party successfully matches the login credentials to an existing account.
Credential stuffing is a scary and dangerous attack technique that has quickly become the number one method of attacks used by cybercriminals. In fact, this year’s Verizon’s 2017 Data Breach Investigations Report states that 81% of organizations have reported hacker-related breaches by an unauthorized party leveraging either stolen or weak passwords. The number of credential misuse incidents is up 18% from Verizon’s 2016 report – making credential stuffing the most common attack technique. With over three billion records being leaked to the dark web last year, credential stuffing has quickly outgrown other attack methods and become a top priority for cybersecurity professionals to defend.
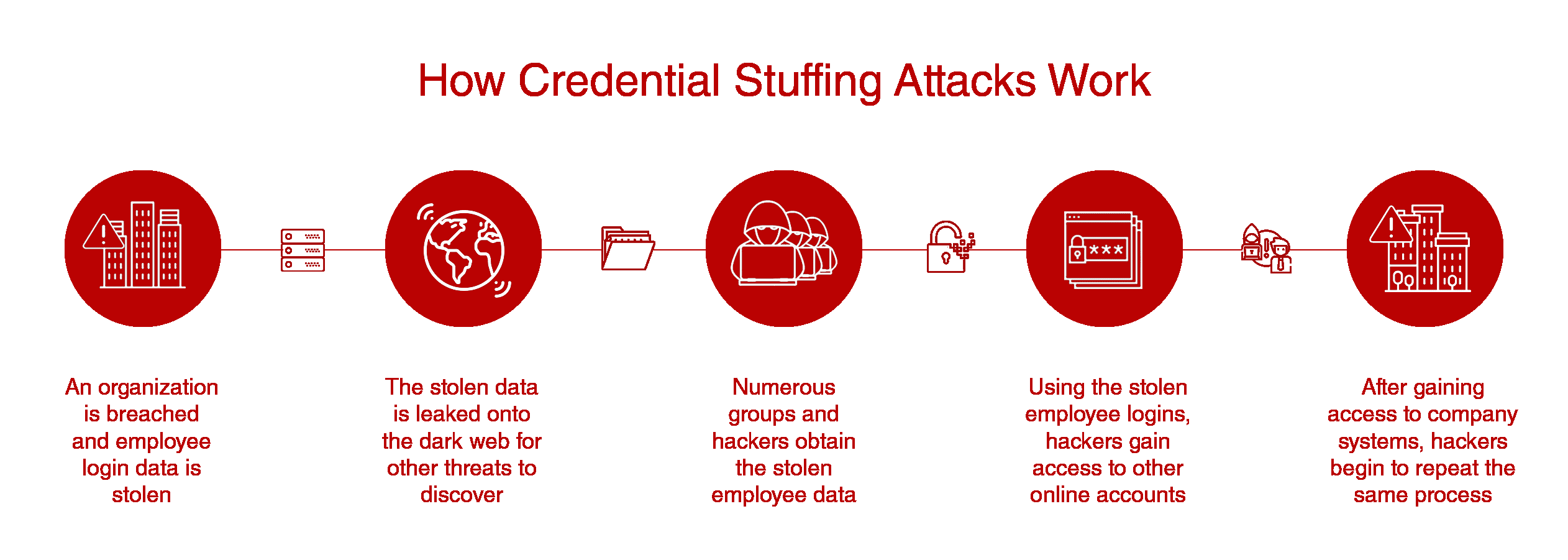
How Are Credentials Stolen?
There are four common ways in which hackers and cybercriminals obtain large lists of stolen user logins and information for targeted credential stuffing attacks.
1. Stolen Databases – The most common and easiest method of access to a large amount of user credentials is obtaining a stolen database of usernames and passwords that has been leaked onto the dark web – the part of the Internet where typically illegal activities take place. Once a large database (e.g. Dropbox – 70 million users, Myspace – 164 million users) of credentials is stolen and leaked to the dark web, hackers can purchase or trade for direct access to millions of user logins ready to be used within a credential stuffing attack.
2. Leaked Databases – Equally as dangerous as a stolen database, leaked databases happen when transferring data from within an organization (or individual) to an external destination such as a data center. Although often unintentional, data leaks provide cybercriminals with public access to user data including usernames and passwords.
3. Phishing Attacks – Although at a much smaller volume, yield hackers with stolen credentials by targeting users with email spam including phishing links. Even though the smaller amount seems to be less dangerous, phishing attacks give hackers plaintext passwords and usernames, which are extremely susceptible to successful unauthorized login attempts.
4. Botnets – Lastly, cybercriminals use Botnets and browser injectors to steal login credentials. Botnets are used to gather and collect user login information as a user enters their information into fields online. The botnet software lives on an infected browser and captures information shared by numerous users. This technique is difficult to detect and defend against – especially if the affected browser does not notice the botnet software.
How Can Credential Stuffing Impact Your Company?
You may look at credential stuffing as a threat that will only impact individuals. However, many of the credentials found within each stolen database are directly associated with employees using the exact same or similar iterations of login credentials for work and personal accounts. Although you may have strict company policies forbidding employees to use their work email or credentials to sign up for services online, that doesn’t necessarily prevent them from doing so. And, if their work email or credentials get hacked, that puts your company’s proprietary information, customer lists and even financial documents at a higher risk of being compromised.
Large companies including Sony, Amazon, Ebay and many others have fallen victim to numerous cybercrimes through unauthorized system access. Hackers were successful in exploiting private communications, lists and networks by leveraging stolen employee login credentials to bypass any computer security walls.
How To Defend Against Credential Stuffing
There are a few quick changes anyone can do to defend against credential stuffing attacks:
- Create Unique Passwords – The most important step to take when beefing up your security is using unique and strong passwords or passphrases for each site, making sure that previously used passwords from other sites are not being replicated elsewhere.
- Enable Two-Factor Authentication – This simple (and often overlooked) security feature provides users with an additional layer of security that requires something that only a specific user has on them, i.e. a security code that is sent to a device in order to access an account.
- Use a Password Manager – By using a password manager like LastPass or PassPack, individuals can create unique and strong passwords for their online accounts inside a secured online password vault without needing to memorize passwords or passcodes.
- Discover and Prevent with HEROIC – Through HEROIC’s enterprise security platform EPIC, organizations can discover compromised employee logins, prompt users to reset compromised logins and prevent employees from using accounts involving compromised data moving forward. Additionally, EPIC offers real-time access to the world’s largest database of compromised credentials and includes real-time credential monitoring as well as immediate notifications based on 1-5 million leaked accounts added to the database every day.
To learn more about how your organization can protect against credential stuffing attacks, contact HEROIC today!
Request A Demo
Submit the form below to see how HEROIC EPIC can help your organization discover, remediate and protect against credential stuffing attacks.