HEROIC GUARDIAN
Unified protection for home users and families









360 Protection For The Entire Family

Protect & Monitor Your Identity
See when your Emails, Passwords, Usernames, Phone Numbers, and IP Addresses have been compromised on the Dark Web.

Secure your Internet and Filter websites
Connect your router to HEROIC’s Internet Security to filter out domains, keep your network secure, and choose what you want people to see.

Protect Yourself against new Cyberthreats
Get Access to core features to protect you and your family from hackers and compromised credentials.
More than Antivirus
Breach Monitoring
Get Instant Details when Your data is Leaked on the Dark Web
Stay ahead of cyber threats with real-time breach monitoring. Guardian scans the dark web to identify when your data has been leaked, providing instant details about the exposure. From compromised passwords to sensitive information, our platform empowers you to act swiftly and mitigate risks before they escalate.
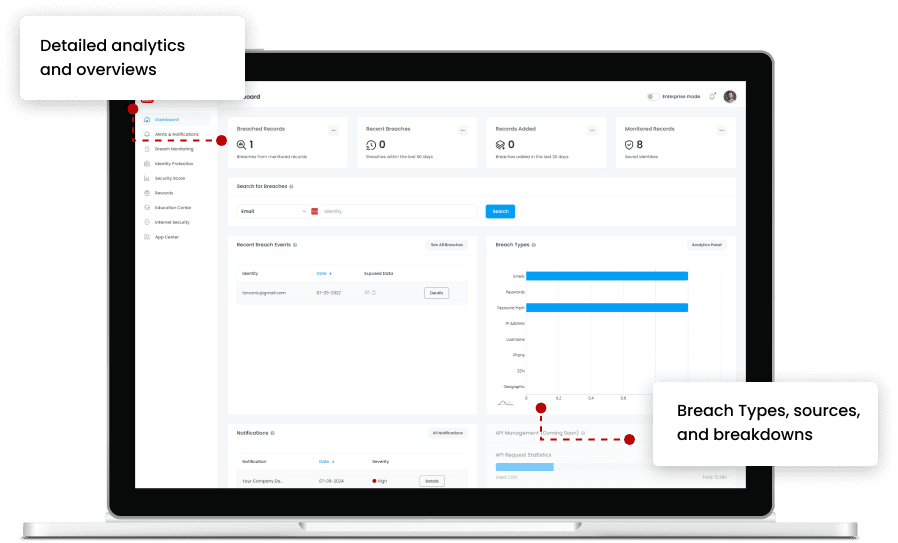
Identity protection
Get alerts when your Social Security has been Used
Protect your personal identity with powerful alerts for suspicious activity. Whether it’s your Social Security number being used without authorization or other critical identity breaches, Guardian notifies you immediately so you can take the steps necessary to safeguard your information and prevent fraud.
Identity protection
Secure your internet with Filters, Domain Blocking, and more.
Ensure a safer online experience with advanced security tools. Guardian offers customizable internet filters, domain blocking, and other features to protect your network from malicious sites and content. With Guardian, you can browse confidently, knowing your digital environment is secure.

Education Center
Stay up to date on new threats and how to stay safe
Stay informed and prepared with Guardian’s comprehensive education center. Learn about emerging cyber threats, security best practices, and tools to protect yourself online. By staying informed, you’ll have the knowledge needed to navigate the digital world securely and confidently.
Core Platform Features
Personalized AI
Largest Hack Database
Robust API Integration
Integrated Apps
Real-Time Alerts
Data Breach Search
Security Education
Internet Monitoring & Filters
Identity Theft Protection
Security Score
Antivirus
VPN

Baniluz
In March 2023, Baniluz, a Spanish e-commerce platform specializing in bathroom furniture and lighting products, faced a data breach involving approximately 1 thousand unique email addresses and full names. This incident underscores the critical importance of robust cybersecurity measures to protect sensitive user information and prevent future breaches. Proper cybersecurity practices are essential to safeguarding personal details and ensuring digital platforms remain secure against potential threats.

Stickam
In 2012, Stickam, a US video-sharing and live streaming platform, experienced a data breach exposing around 350,000 unique email addresses, as well as usernames and MD5 hashed passwords. This event emphasizes the critical role of cybersecurity in protecting user information from potential threats.

Base-One Silcare
In July 2023, Base-One Silcare, a Romanian e-commerce platform specializing in professional nail care and beauty products, suffered a data breach affecting approximately 2400 records. The exposed data included around 2,200 unique email addresses and full names. This incident underscores the critical importance of robust cybersecurity measures to protect sensitive user information and safeguard against future breaches.

Bania
In March 2023, Bania, a Bulgarian e-commerce platform specializing in bathroom, kitchen, and garden products, faced a data breach involving approximately 2,700 records. The data contained 208 unique email addresses and full names. This incident underscores the critical importance of robust cybersecurity measures to protect sensitive user information and prevent future breaches. Proper cybersecurity practices are vital to safeguarding personal details and ensuring digital platforms remain secure against potential threats, thereby maintaining customer trust and preventing further incidents.

A to Z Apparel
In October 2022, A to Z Apparel, an ecommerce platform, experienced a data breach involving approximately 4,700 records containing roughly 1,500 unique email addresses, full names, phone numbers, and physical addresses. This incident highlights the critical importance of robust cybersecurity measures to protect sensitive user information and prevent future breaches. Proper cybersecurity practices are essential to safeguarding personal details and ensuring digital platforms remain secure against potential threats.

News of Legends
In 2020, News of Legends, a US-based platform for League of Legends, experienced a data breach exposing approximately 700,000 records. The data contained around 72,000 unique email addresses and PHPass hashed passwords. The incident highlights the importance of implementing robust cybersecurity measures to protect sensitive user information from potential threats.

Scam.com
In 2016, Scam.com, a US forum discussing scams, suffered a data breach exposing over 360,000 records containing over 172,000 unique email addresses, usernames, and MD5 hashed and salted passwords. The breach could have enabled attackers to launch phishing or identity theft campaigns. Implementing strong cybersecurity measures is crucial to safeguard sensitive user data and prevent future breaches from leading to scams or financial loss.

DaniWeb
In December 2015, DaniWeb, a US-based online community for developers and IT professionals, suffered a data breach affecting approximately 941 thousand records. The exposed information included email addresses, usernames, IP addresses, and MD5 hashed and salted passwords. This incident highlights the importance of robust cybersecurity measures to protect sensitive user data.

Mop.com (猫扑)
In 2020, Mop (猫扑), a Chinese online forum, suffered a data breach exposing approximately 2 million records. The exposed data included over 1.8 million unique emails addrsses as well as passwords stored in plain text. Proper cybersecurity measures are essential to protect sensitive information from being accessed or leaked, as such breaches can lead to identity theft and financial fraud.

Zoloto585
In April 2023, Zoloto585, a Russian e-commerce platform, suffered a data breach exposing approximately 14 million records. The data contained over 4 million unique email addresses, as well as full names, phone numbers, genders, and birthdays. This underscores the critical need for robust cybersecurity measures to prevent such breaches and safeguard sensitive information.

Woman and Home
In 2020, Woman & Home, a UK-based digital lifestyle magazine, suffered a data breach exposing over 46,000 records containing email addresses, usernames, IP addresses, and MD5 hashed and salted passwords. This incident underscores the importance of robust cybersecurity measures to safeguard sensitive information from potential breaches.

Grain de Beauté
In March 2023, Grain de Beauté, a French ecommerce website, experienced a data breach affecting close to 570 records containing email addresses and full names. This incident underscores the critical importance of robust cybersecurity measures to protect sensitive user information and prevent future breaches. Proper cybersecurity practices are essential to safeguarding personal details and ensuring digital platforms remain secure against potential threats, thereby maintaining customer trust and preventing further incidents.

YotePresto
In June 2020, the Mexican lending platform YotePresto experienced a data breach that impacted over 1.4 million customers. The breach exposed approximately 1.4 million unique email addresses, as well as IP addresses, and passwords stored as bcrypt hashes. This incident underscores the critical importance of strong cybersecurity measures to protect user data and prevent such breaches.

Devir Americas
In March 2023, Devir Americas, an US-based ecommerce platform specializing in tabletop games, faced a data breach affecting approximately 15,000 records containing 490 unique email addresses, full names, and geographical locations. This incident underscores the critical importance of robust cybersecurity measures to protect sensitive user information and safeguard against future breaches. Proper cybersecurity practices are essential to prevent unauthorized access and ensure the security of digital platforms, thereby maintaining customer trust and preventing further incidents.

Xbox360
In August 2023, the official website for Xbox, the gaming brand owned by Microsoft Corporation, suffered a data breach that impacted 1 million users. The compromised data included email addresses and plaintext passwords. This incident highlights the urgent need for secure password storage and comprehensive cybersecurity measures in the gaming industry, where user accounts often contain both personal and financial information.

The World Association for Waterborne Transport Infrastructure
In August 2023, the official website of PIANC (The World Association for Waterborne Transport Infrastructure), which provides technical guidance and best practices for the sustainable development of waterborne transport infrastructure, suffered a data breach that impacted approximately 3,536 users. The compromised data included email addresses and phone numbers. This breach highlights the necessity for professional organizations—especially those involved in global infrastructure—to implement strong cybersecurity measures to protect the sensitive contact information of their members and partners.

Yemek Sepeti
In August 2023, Yemek Sepeti, Turkey’s pioneering online food ordering and delivery platform, experienced a data breach that affected approximately 12,693 users. The compromised data included phone numbers, full names, and physical addresses. This incident highlights the necessity of implementing stringent cybersecurity protocols in online delivery services, where user location and identity information are regularly processed and stored.

Game Odin
In January 2023, Game Odin, a Taiwanese e-commerce platform specializing in games, experienced a data breach involving approximately 172,000 records. The exposed data included 672 unique email addresses, usernames, and MD5 hashed or plain text passwords. This incident highlights the critical need for robust cybersecurity measures to protect sensitive user information and prevent future breaches.

CMeShine
In December 2022, CMeShine, a US-based social media network for dancers and dance studios, experienced a data breach involving approximately 700,000 records. The exposed data included around 1,900 unique email addresses, full names, usernames, phone numbers, physical addresses, birthdays, genders, and bcrypt hashed passwords. This incident highlights the critical need for robust cybersecurity measures to protect sensitive user information and prevent future breaches.

Fokus Fit
In January 2023, Fokus Fit, a Brazilian e-commerce platform for fitness equipment and accessories, faced a data breach affecting approximately 81k records. The exposed data included around 21,000 unique email addresses, full names, physical addresses, and phone numbers. This incident underscores the critical importance of robust cybersecurity measures to protect sensitive user information and prevent future breaches. Proper cybersecurity practices are crucial to safeguarding personal details and ensuring digital platforms remain secure against potential threats.




/qr-code.png)