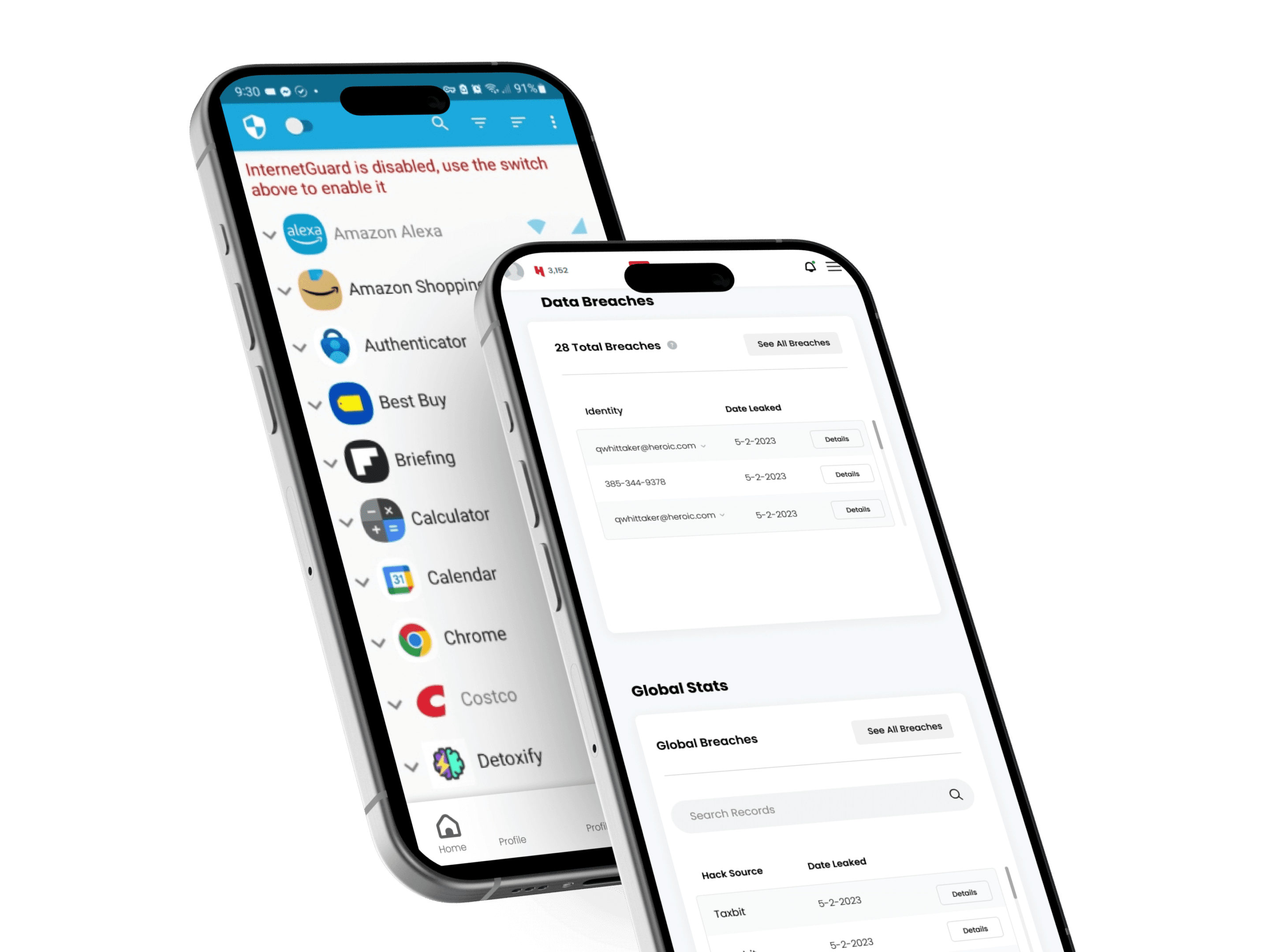
Has your personal information been leaked in a databreach?
Search over 400+ Billion records on Darkhive, HEROICS Database fo compromised credentials.
🔍 Live Recent Searches
Unique fingerprints of over 15 billion email addresses
The Worlds Largest Breach Database
Over 15 Billion Records
Our Data Collection Process
Our lives rely on technology. We use it to do our jobs, entertain ourselves and stay connected. As technology continues to grow, our reliance on that technology does as well.

An organization’s employee and/or customer databases are either stolen or leaked by a malicious party

The compromised data is placed on the dark web where malicious threats and attackers obtain the data

HEROIC threat analysts discover the leaked and compromised data in hacker forums, paste bins, etc.

The data is then verified, cleaned and uploaded into HEROIC DarkHive™ for search and reporting

Users and organizations using HEROIC receive account alerts and other remediation actions

/includes/qr-code.png)